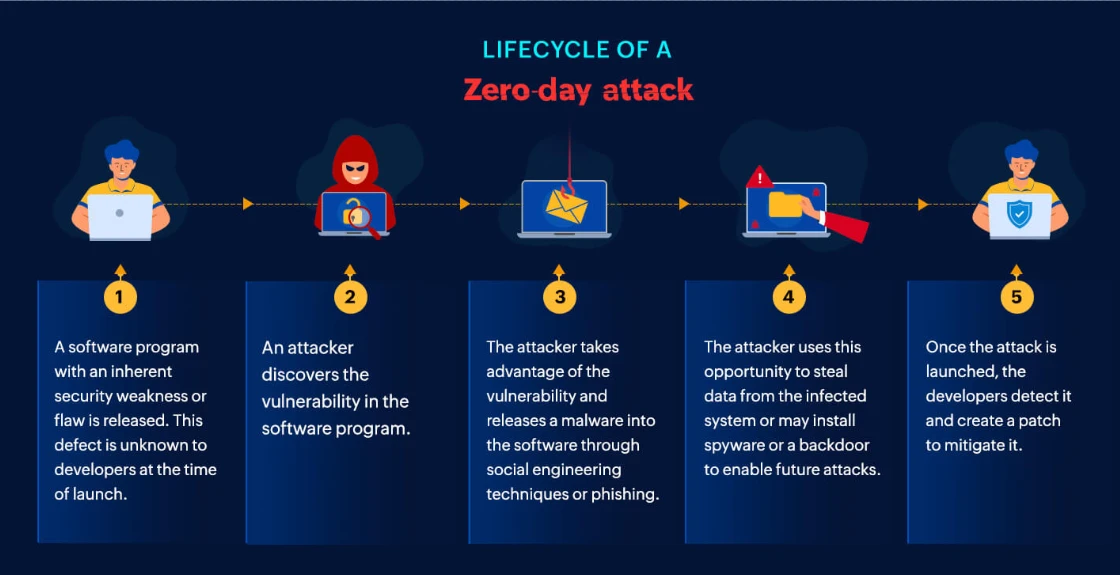
What are Zero-Day Exploits
A Zero-Day exploit is a cyberattack that targets a previously unknown vulnerability in software, hardware, or firmware. The term "Zero-Day" refers to the fact that developers have Zero-Days to fix the flaw before attackers can take advantage of it. These exploits are particularly dangerous because they occur before security patches or updates are available, leaving systems exposed to potential breaches.
Zero-Day vulnerabilities exist in all types of digital environments, including operating systems, applications, cloud platforms, and even Internet of Things (IoT) devices. Cybercriminals, state-sponsored hackers, and even security researchers actively hunt for these undisclosed weaknesses. Once a vulnerability is discovered, it can be exploited in various ways, including injecting malware, gaining unauthorized access, or executing arbitrary code on a compromised system.
Zero-Day exploits are highly valuable on the dark web, where cybercriminals buy and sell them in underground markets. Some hackers use them for financial gain, while others use them for espionage or sabotage. Governments and intelligence agencies may also leverage Zero-Day exploits for cyber warfare or surveillance.
Attackers often deliver Zero-Day exploits through phishing emails, malicious websites, or drive-by downloads. These methods trick users into running malicious code, which then exploits the vulnerability. Since traditional security tools like antivirus software and firewalls rely on known threat signatures, they may fail to detect these attacks, making them particularly difficult to stop.
The impact of a Zero-Day exploit can be severe. Organizations that fall victim may suffer from data breaches, system downtime, financial losses, and reputational damage. Some of the most notorious cyberattacks in history have involved Zero-Day exploits, including the Stuxnet worm, which targeted Iran's nuclear facilities, and the WannaCry ransomware attack, which spread globally by exploiting an unpatched Windows vulnerability.
Defending against Zero-Day exploits requires a proactive security approach. Threat intelligence, behavior-based detection, and endpoint protection solutions can help identify suspicious activities that may indicate an exploit attempt. Network segmentation, regular security updates, and strict access controls can also reduce the attack surface. Additionally, organizations can implement Zero Trust security models to limit unauthorized access and mitigate the impact of an exploit.
While Zero-Day exploits will always be a risk in cybersecurity, staying informed and investing in advanced security measures can help minimize exposure. By continuously monitoring systems, applying security best practices, and leveraging cutting-edge threat detection technologies, businesses and individuals can strengthen their defenses against these unpredictable threats.
Real-World Examples of Zero-Day Attacks
Real-world examples of zero-day attacks highlight how dangerous and disruptive these threats can be, especially when they exploit unknown vulnerabilities before developers have a chance to patch them. Zero-day attacks are particularly effective because they take advantage of software flaws that are not yet documented or publicly disclosed. This gives attackers a significant advantage, allowing them to breach systems, steal data, or disrupt operations with little to no resistance. Organizations across industries—from government and healthcare to finance and tech—have all been affected by zero-day attacks, making it a top concern for cybersecurity professionals.
One of the most infamous zero-day attacks was the Stuxnet worm, discovered in 2010. Believed to be a joint effort by nation-state actors, Stuxnet targeted Iran’s nuclear program by exploiting multiple zero-day vulnerabilities in Windows systems. It was designed to sabotage uranium enrichment operations by causing physical damage to centrifuges, all while avoiding detection. Stuxnet demonstrated how zero-day attacks could cross the digital-physical boundary and cause real-world harm.
Another major example is the Microsoft Exchange Server zero-day attacks in early 2021. Hackers exploited four previously unknown vulnerabilities in Microsoft’s email server software, allowing them to gain access to email accounts, install malware, and take control of affected systems. These exploits were attributed to a state-sponsored threat group and impacted tens of thousands of organizations globally. The attack exposed how critical infrastructure and sensitive communication systems could be compromised before a patch was made available.
In 2014, a zero-day vulnerability known as Heartbleed was discovered in the widely used OpenSSL cryptographic library. While not a traditional exploit used by attackers before discovery, its presence for years meant that attackers could have silently accessed encrypted data like passwords, private keys, and other sensitive information. Heartbleed affected a massive portion of the internet and led to a global scramble to patch systems and reissue security certificates.
Another significant incident occurred in 2021 with Google Chrome’s zero-day vulnerabilities, where multiple bugs were actively exploited in the wild before patches were released. Attackers leveraged these browser vulnerabilities to carry out drive-by downloads, execute malicious scripts, and potentially gain control over a user's device—underscoring how even end-user applications can be targeted.
Zero-day attacks continue to be a major threat because they leave no window for traditional defenses to react. These incidents emphasize the need for proactive security models like Zero Trust, which assume breach, monitor continuously, and limit access to reduce the damage zero-day exploits can cause before detection and response can occur.
Zero-Day Exploits vs Known Vulnerabilities
Zero-Day exploits and known vulnerabilities are both security risks that cybercriminals exploit, but they differ in how they are discovered, addressed, and defended against. Understanding these differences is crucial for organizations and individuals looking to strengthen their cybersecurity posture.
A Zero-Day exploit targets a vulnerability that has not yet been publicly disclosed or patched by the software vendor. Because no security update exists to fix the flaw, attackers can exploit it without interference. Zero-Day vulnerabilities are particularly dangerous because they give hackers a head start—before developers even know the weakness exists. Cybercriminals often use these exploits to launch sophisticated attacks, gain unauthorized access, or deploy malware. Since traditional security solutions rely on known threat signatures, they often fail to detect Zero-Day attacks, making them highly effective for cybercriminals.
On the other hand, known vulnerabilities refer to security weaknesses that have already been identified and publicly disclosed. Vendors typically release patches, security updates, or software fixes to address these vulnerabilities. However, even after a fix is available, many organizations fail to apply patches promptly, leaving their systems exposed to attacks. Cybercriminals frequently scan networks for outdated software, exploiting unpatched vulnerabilities to gain access. The longer a vulnerability remains unpatched, the greater the risk of exploitation.
The primary difference between these two types of vulnerabilities is awareness. With known vulnerabilities, security professionals and vendors have the opportunity to address the issue before widespread exploitation occurs. In contrast, Zero-Day exploits give attackers the advantage, allowing them to strike before any security defenses can be implemented.
A key challenge in preventing Zero-Day exploits is that traditional antivirus software and firewalls rely on existing databases of known threats. Since Zero-Day attacks target unknown weaknesses, these defenses often fail. Organizations need advanced security solutions, such as behavior-based detection, machine learning algorithms, and Zero Trust architectures, to identify and mitigate these threats in real time.
In contrast, defending against known vulnerabilities is more straightforward—regular software updates, patch management policies, and vulnerability scanning can significantly reduce risk. Cybersecurity frameworks like the Common Vulnerabilities and Exposures (CVE) system provide public databases where security teams can track known vulnerabilities and apply fixes accordingly.
Ultimately, both Zero-Day exploits and known vulnerabilities pose serious threats, but their impact depends on how quickly organizations respond. By maintaining a proactive security strategy that includes continuous monitoring, patching known vulnerabilities, and leveraging advanced threat detection for unknown exploits, businesses can better protect themselves against evolving cyber threats.
How Organizations Can Detect Zero-Day Attacks
Detecting Zero-Day attacks is one of the most challenging aspects of cybersecurity because these exploits target unknown vulnerabilities, meaning there are no existing security patches or predefined threat signatures to identify them. Unlike traditional cyber threats, which rely on previously known patterns, Zero-Day attacks require a proactive, multi-layered approach to detection and mitigation. Organizations must employ advanced security measures, behavior-based analytics, and continuous monitoring to identify and respond to these elusive threats before they cause significant damage.
One of the most effective ways organizations can detect Zero-Day attacks is through behavioral anomaly detection. Since Zero-Day exploits do not have known signatures, security tools must analyze network traffic, user behavior, and system activity to identify suspicious patterns. Machine learning and artificial intelligence (AI) play a crucial role in this approach by learning what constitutes normal behavior and flagging deviations that could indicate a Zero-Day attack. For example, if an application suddenly starts executing unusual commands or accessing restricted files, it could signal an exploit in progress.
Another key method is sandboxing and threat simulation. By running applications and files in an isolated virtual environment, organizations can observe their behavior without risking compromise to the main system. If an application attempts to execute suspicious actions—such as modifying system files, escalating privileges, or establishing unauthorized network connections—it may be a sign of a Zero-Day exploit. Security solutions that incorporate sandboxing can quickly detect and analyze potential threats before they infiltrate production environments.
Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR) solutions provide another layer of protection. These advanced security tools continuously monitor endpoints and network traffic for suspicious activity. If a Zero-Day exploit attempts to install malware, escalate privileges, or move laterally across a network, EDR and XDR platforms can detect and block the attack in real time. Additionally, these tools provide forensic analysis to help security teams understand the nature of the exploit and respond accordingly.
Threat intelligence is also critical in detecting Zero-Day attacks. Organizations can leverage Threat Intelligence Feeds (TIFs) and participate in industry-sharing initiatives to stay informed about emerging threats. By analyzing global attack trends and monitoring indicators of compromise (IoCs),security teams can anticipate potential Zero-Day threats and enhance their defense strategies.
Finally, Zero Trust security models can help mitigate the impact of Zero-Day attacks. By enforcing strict access controls, continuously verifying user and device trustworthiness, and limiting network privileges, organizations can minimize the attack surface and contain potential threats before they spread.
While detecting Zero-Day attacks is inherently difficult, a combination of behavior-based detection, AI-driven analysis, sandboxing, endpoint monitoring, and threat intelligence can significantly improve an organization’s ability to identify and mitigate these stealthy cyber threats.
The Future of Zero-Day Threats
The future of zero-day threats is increasingly concerning as cybercriminals, nation-state actors, and advanced persistent threat (APT) groups continue to develop more sophisticated techniques to exploit undiscovered software vulnerabilities. As the digital landscape grows in complexity—with the expansion of cloud computing, Internet of Things (IoT) devices, remote work, and AI-powered systems—the number of potential vulnerabilities also rises. This means that the opportunities for zero-day attacks will likely increase, making them one of the most dangerous and difficult-to-defend cyber threats of the future.
One of the key trends shaping the future of zero-day threats is the commercialization of cybercrime. In recent years, the underground market for zero-day vulnerabilities has expanded significantly. Vulnerabilities are being bought and sold for millions of dollars by brokers, hackers-for-hire, and even private companies. As a result, attackers with sufficient resources can purchase high-impact zero-days and deploy them in targeted campaigns, often before vendors are aware of the flaws.
Another factor is the increasing use of automation and artificial intelligence by threat actors. These technologies allow cybercriminals to scan for vulnerabilities, test exploits, and launch attacks at an unprecedented scale and speed. AI can also help attackers hide their activities more effectively, making zero-day exploits harder to detect and respond to in real time. This arms race between attackers and defenders will continue to escalate as both sides leverage machine learning to gain an advantage.
The growing reliance on open-source software and third-party components in enterprise applications is another area of concern. While open-source tools accelerate development and innovation, they also expand the attack surface and introduce new supply chain risks. Vulnerabilities in widely used libraries or components—such as the Log4j incident—can be exploited before the wider community is aware, impacting thousands or even millions of systems across industries.
In response to these evolving threats, security strategies will need to become more proactive and resilient. Zero Trust architecture will play a critical role in mitigating the impact of zero-day threats by reducing the scope of access, continuously verifying trust, and limiting lateral movement within networks. Organizations will also need to invest in threat intelligence, real-time behavioral analytics, and automated detection and response tools to identify and contain zero-day exploits before they can cause significant damage.
In summary, the future of zero-day threats will be defined by increasing complexity, rapid exploitation, and global impact. To stay ahead, organizations must assume that vulnerabilities exist, implement proactive defense strategies like Zero Trust, and focus on early detection, containment, and continuous monitoring. Only by building resilient, adaptive cybersecurity frameworks can businesses and governments hope to stay protected in an era where zero-day threats are the new normal.