Powering You to
Power the World
The energy sector is the backbone of global infrastructure, making it a prime target for cyberattacks. Xcitium’s Zero Trust solutions deliver robust security tailored to the unique challenges of the energy industry, protecting critical systems, operational technology (OT), and sensitive data from ransomware, breaches, and advanced threats. Ensure uninterrupted energy delivery, regulatory compliance, and resilience against evolving cyber risks with Xcitium’s innovative security platform. Safeguard your operations and power the future securely with Xcitium.
Manage your evolving attack surfaces; prevent, detect, isolate, and remediate threats across endpoint, cloud, identity, and beyond before they attack the supply chain.
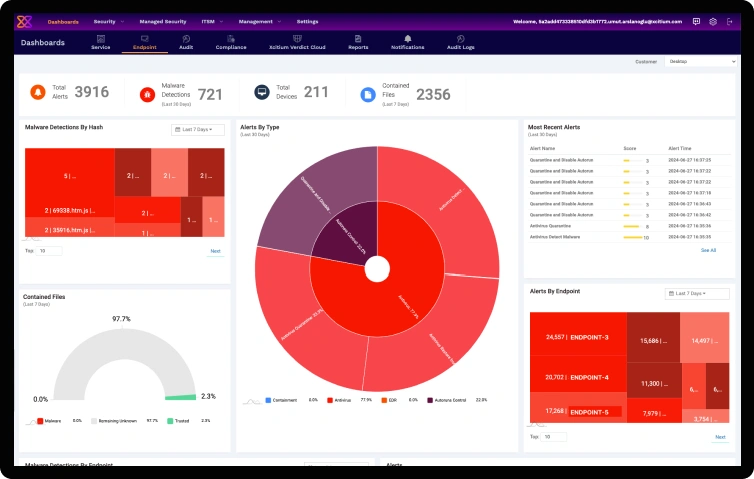
A Unified Security Approach for Even the Most Diverse, Distributed Attack Surfaces.
Organizations around the world rely on Xcitium’s innovative solutions to help bring zero-trust posture from their endpoints to their cloud, under a single pane of glass.
Review weekly proof of our zero trust containment protection. New malware and ransomware always start their lives as Unknowns. That’s why detection-based products miss these detection and allow breaches to occur. Review weekly proof of our zero trust containment here.
of active devices with potential malicious activity (in-containment)
of active devices on known good state (no unknowns)
of active devices with infection or breach
of the unknown that turn out to be malware









