If you wonder who invented EDR, in 2013, Anton Chuvakin of Gartner introduced the term "endpoint threat detection and response" for "tools mainly aimed at detecting and investigating suspicious activities (and traces of such) other issues on hosts/endpoints." Endpoint detection and response is now a common term for people.
Why EDR Is Important?
Cyber-attacks have been increasing at an exponential rate since the COVID-19 breakdown. These cyber-attacks typically target organizations/individuals with digital assets, including High-Value Targets. Cyber-attackers strive to successfully target and attack your company's endpoints because it provides a clear path to the target. Advanced attacks, such as APT, consider the endpoint the most fragile link in the security perimeter. They may need to delete or hold your data for ransom, override your machines and configurations, use them in a botnet, conduct DDoS attacks, and much more. EDR is a term that refers to Endpoint Detection and Response, but who invented EDR? Let's find out who invented EDR.
What is EDR
Before we delve into details lets know what EDR is Who Invented EDR? Endpoint detection and response (EDR), also known as endpoint detection & threat response (EDTR), is a form of endpoint security mechanism that continuously monitors end-user devices for cyber threats such as ransomware and malware.
How does EDR work?
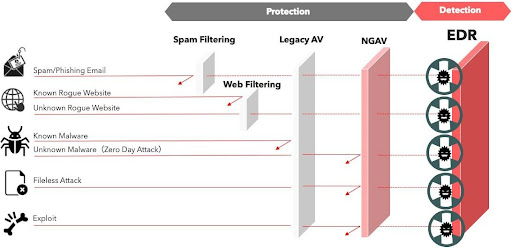
Who Invented EDR has this theory in mind that EDR security solutions analyze events from desktop PCs, mobile devices, laptops, servers, and even IoT and cloud workloads to detect suspicious activity. They create alerts to help security operations analysts find, investigate, and resolve issues. EDR tools collect telemetry data on suspicious activity and may supplement it with contextual information from correlated events. EDR, through these functions, helps incident response teams reduce response times and, ideally, eliminate threats before they cause damage.
If you still wonder who invented EDR, Endpoint detection and response (EDR) first appeared in 2013 to aid forensic investigations that required extremely detailed endpoint telemetry to analyze malware and understand exactly what an attacker did to a compromised device. It has evolved to include a broader range of features and typically includes endpoint protection or antivirus abilities.
What are the Components of an EDR
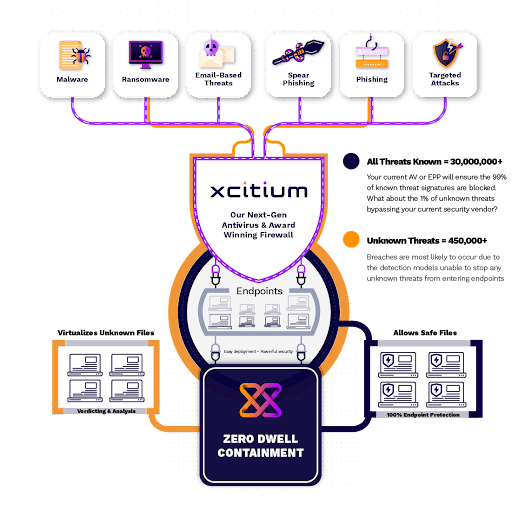
EDR security gives an organization a centralized platform for collecting, organizing, and analyzing data from connected endpoints. It can synchronize responses and alerts to immediate threats. Apart from the point of who invented EDR, this requires the involvement of three elements:
Endpoint Agents
These agents, installed on your endpoints, collect and monitor data. This includes information about which processes are running, how much activity is happening on the endpoint, what the endpoint's connections are, and how data is transferred to and from the endpoint, etc.
Automated incident response
Apart from knowing who invented EDR, one should also know that EDR allows you to include custom rules designed by you and your team to identify threats. The automatic responses can then be triggered based on these rules. The automated response can both recognize and categorize the threat. Then it can take action, such as isolating the infected machine and sending an alert to administrators for further action.
Analysis
Who Invented EDR knew that EDR is also capable of analyzing endpoint data in real time. Endpoint data is analyzed in real-time during analysis. This allows the EDR system to quickly diagnose threats, even if they do not match preconfigured threat parameters. After the threat has been dealt with, analysis utilizes forensic tools to investigate the nature of the threat and how the attack was carried out.
What are the 3 Benefits of EDR
Overall, EDR solutions can go a long way toward assisting businesses in preventing significant damage from being caused by hackers. After knowing who invented EDR, let's go through some of the most important ways EDR can help are as follows:
Quickly identify and stop threats
Apart from knowing who invented EDR, one should also know that EDR tools are generally capable of identifying and stopping cyber threats quickly, often via automation. EDR tools continuously monitor endpoint activity to detect suspicious or threatening activity in real-time. Once a threat has been identified, EDR can isolate and deflect attacks from internal and external sources, thereby protecting endpoint devices.
Proactively hunt threats
Apart from knowing who invented EDR, one should also know that EDR tools can quickly identify and stop cyber threats in part because these solutions often involve proactively hunting down new threats that other cyber security tools may miss. Cyber threat hunting scours your environment for malicious actors who have slipped past your interim endpoint security defenses.
Gain the support of security experts
Who Invented EDR also had clarity that aside from the automated capabilities that EDR tools provide for detecting and blocking threats, EDR solutions often enhance an organization's ability to analyze security risks on a human level. Many cyber security software vendors provide managed EDR tools, which provide other businesses with the support of a security operations center (SOC) to manage the tool and review incidents.
Who Invented EDR?
After knowing who invented EDR, choose Xcitium EDR Services for superior defense against crippling cyber-attacks. To combat advanced threats, we provide clear visibility into your security situation and implement the highest level of detection and response. Contact us immediately to learn more about who invented EDR and get started.