Endpoint detection and response tools are making great buzz on the internet these days. Organizations of every kind and type are using them to secure their laptops, computers, desktops, workstations, and other devices.
An EDR is an endpoint system that monitors all the endpoint data and collects it on the centralized system for further analysis and investigation to prevent malware attacks. This software is becoming an integral part of the cybersecurity of your organization.
Before you invest in this tool, you should know how valuable EDR data is for the security team. Let's continue reading and find out.
What is EDR Data?
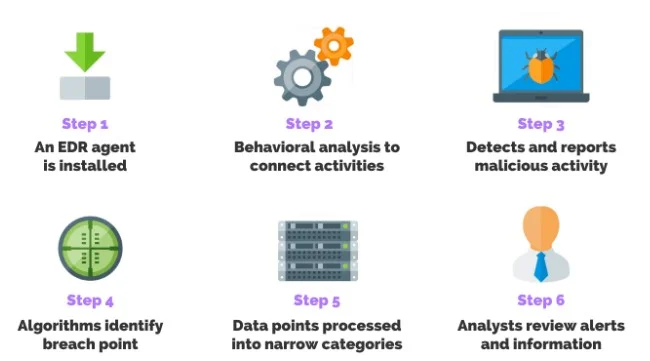
Once an EDR agent is installed on all your endpoints, it continuously monitors them in real time, collects data from them, and transfers it to a centralized dashboard. Now your security team can open a single console and look into all the activities across endpoints. They don't need to check individual devices.
The big plus of this endpoint protection tool is that the team controls each connected device (offline or online) from one dashboard.
Now the question is what kind of data is recorded by EDR. This software looks for malicious programs and processes to prevent malware attacks. It accomplishes this by recording processes and details of programming running on your endpoints.
Besides, it also records file names that you access. It also keeps a record of logged-in information to prevent unauthorized user access.
How Helpful is EDR Data for the Cybersecurity Team?
This software collects all the activity info and helps the cybersecurity team in many different ways. Let's find out more.
• Great Amount of Visibility to Stop Threats
The biggest plus of endpoint activity info is that all the vulnerability and weakness of the system is quite visible to the team. They don't need to run security scans or perform penetration testing to find out where the problem lies and where they need to fix it.
All the endpoint activities are visible to them through endpoint protection software. Within a few clicks, they can patch these vulnerabilities and prevent an attack from happening.
• Current Event Analysis to Accelerate the investigation
An endpoint tool is designed with machine learning, behavior analysis technology, and signature-based detection technology. This software collects activities details and performs analysis to identify threats. Security teams can spend hours and weeks identifying threats with all these technologies.
All the information collected from the endpoint is stored on the cloud platform, especially when you use Open EDR. Now your team can get the information they want by searching this database. They can unlock the complete event tree structure. It helps them understand how a bad actor got access to the system and, what endpoint was got affected when.
No matter your questions regarding an event or situation, all the information will be provided from the database.
Your security analyst won't have to find it manually. Since every piece of information is a click away, the team can investigate and remediate a threat faster.
Historical EDR Data Analysis to Prevent Similar Attacks
When you have an endpoint detection system, it keeps full track of all security-related events. And it also collects other activities' info, such as driver loading, registry modification, URL access, memory access, disk access, and process creation.
Your cybersecurity team can leverage this data and information well to prevent future attacks. They can dig into historical activity details and discover the exact behavior, techniques, and procedure malware uses. Once they identify their techniques, they store them in the database so similar attacks won't happen.
This historical data analysis helps your team big time when getting to know your adversaries. They can look into archive file creation, removable media usage, a summary of administrative tools or executable changes, and other information to prevent malicious attacks.
• Sandbox Data Analysis to Speed up Remediation
When an EDR finds some malicious file, it temporarily quarantines it and sends it to the sandbox. This virtual containment environment runs the malicious file on the endpoint while disconnecting it from the rest of the network.
IT Analyst gets threat alerts, and they can start looking into infected endpoints by analyzing all the codes, files, and process. As a result, they understand the threat and take action against it while leaving zero impact on the overall network.
Wrap up
Finally, you have a clear picture of how EDR data proves helpful for your security team. Whether you want to prevent a malware attack on your system or consider becoming proactive with your cybersecurity approach, you need to leverage this critical info.
