The biggest challenge for the Information security team is getting software to detect known and unknown threats. However, there is yet to be a comprehensive solution. Cybercriminals are savvy and can get past the tools by exploiting system vulnerabilities.
You must know about all detection methods available today, so you can choose one way that works better than others. Let's continue reading and uncover all the details.
Complete Guide
Organizations are exposed to different criminals attack, especially with the emergence of remote work culture. You must determine what vulnerable endpoint a bad actor uses to exploit the system. Threat detection is a process in which software and analyst evaluate the complete IT infrastructure to find any suspicious behavior that may lead to a security breach or malicious event across the network.
It would help if you kept an eye on your endpoint and network activities with the means of threat detection tools so that you can create a strong defense against numerous cyber attacks.
Here are Four Common Detection types :
1- Threat IntelligenceSiganture-based detection is the whole concept of threat intelligence. According to this method, once the system monitors suspicious activity, it compares the code and files with the existing database.
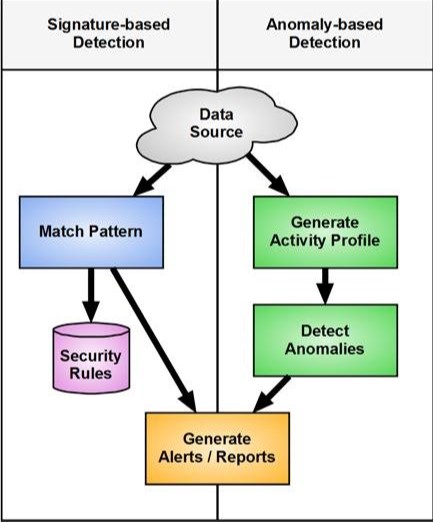
A system based on signature detection keeps a complete record of known threats' signature data. Thereby, it can identify dangers by comparing the data of past and current security events. If the code of a new file matches the code of a known threat, then this program readily stops or deletes it.
Antivirus relies on signature-based detection techniques. It scans a file and finds malware through code-matching techniques.
Although it is the most effective technique, it could be more effective in spotting brand-new malware or novel dangers.
2- Behavior AnalysisIt is a practice where a program can spot suspicious behavior through continuous analysis of user and attacker behavior. For example, if you get an EDR- Endpoint detection and response system, you get software that monitors all endpoints nonstop.
It collects user data and keeps activities logged in a secured cloud-based database. It creates a baseline for the program through this monitoring.
The system knows what's the usual behavior of an endpoint user. For example, what file he accessed, his privileges, location, and timing for using a system. It has all this record as a baseline.
Suppose a threat actor tries accessing this endpoint and downloading or exporting sensitive files. Since it's unusual behavior, the system readily spots this malicious behavior. It readily sends an alert to a security analyst.
And it's not the only response; Xcitium EDR has a patented containment system containing the threat so that malware attack doesn't spread system-wide.
3- Intruder TrapsAnother detection type that your security team employs is an intruder trap. The purpose is to find the real motive behind the attack and also understand the tactics, techniques, and procedures TTPs of an attacker.
In this practice, the security team creates a trap for intruders so that you can stay prepared for a dangerous threat and attack. They intentionally make their system vulnerable, so an attacker takes the bait and exposes its tactics.
4- Threat HuntingIt is another kind of detection where threat hunters actively hunt for malware, ransomware, and other dangers to your organization are exposed to. Hunting aims to uncover new threats and stay prepared for new malware.
It is a proactive cybersecurity approach where your security analyst runs scans and penetration tests to find out where your system is vulnerable and what issues exist. They can patch vulnerabilities and fix the problems so that they no longer make your business vulnerable.
Benefits of Detection
You already understand types; now, the next thing to understand is their benefits.
Reduce Financial ImpactIf your organization experience ransomware, you need to pay the high cost. Besides, your reputation got damaged, and you lost the market trust after an attack. So, once you have the right detection tools, you won't have to deal with any such issue, and it's how you dial down the real impact of cyber attacks.
Prevent AttackThe biggest plus of this technique is that your organization won't experience any zero-day attacks, known viruses, or malware threats.
Data ProtectionYou can't afford to lose your trade secrets or sensitive business data. Can you? Once you employ the right threat identification methods, you can protect your confidential data and information.
Final Words
Finally, you understand all about detection methods. It would be best to have expert cybersecurity analysts who can run advanced tools to prevent attacks on your organization. You won't face financial loss, reputational damage, or regulatory fines.
