Do you know that your organization's endpoints are exposed to cyber attacks such as zero-day, crypto-jacking, and much more? These attacks are common among those businesses that have a remote workforce. Negligence from remote employees can often lead to ransomware and other threats. So, when it comes to protecting your endpoints, EDR is one of the best solutions available. Before investing in this solution, you will surely be interested in how it works. Let's unwrap all the details below:
What Activates an EDR? Complete Guide
Understanding the central concept of this cybersecurity solution is essential, and then it will be easy for you to grasp how it activates.
What is EDR?It is an acronym used for Endpoint Detection and Response system. It monitors all endpoints in real-time and detects, prevents, and responds to potential threats. It is integrated with advanced machine learning and artificial intelligence tool; this system is quite effective in dealing with file and file-less threat actors.
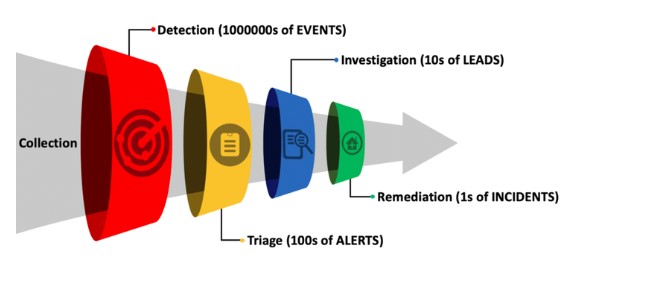
This system uses superior threat intelligence and analysis capabilities to protect your system against malicious attacks. This software monitors all the endpoint's activities and analyzes the behavior. When it detects malicious activities, it contains this threat in a separate containment system.
For example, when you go with XcitiumEDR, it isolates a compromised endpoint and runs its activities in a separate containment system. This quarantine ensures that malware attacks from one endpoint won't spread to another.
Once a malicious attack is detected, an EDR agent will alert IT Administrator. It will automatically respond to a threat if designed with an incident response playbook. A security analyst can check the log activities of endpoints and try to create a complete story behind the attack. Since it also has a threat analytics tool, it becomes easy for your team to analyze a threat and respond to it.
What Activates an EDR?
An EDR solution gets activated when malicious activity is detected on an endpoint. These activities are of varied kinds.
For example:
- An unauthorized person tries to access your endpoint data and file
- The system notices unusual network traffic
- The software detects unexpected changes in the overall system or configuration.
- It may spot some unusual programs running on endpoints.
- A user tries to export a file to another unknown system
- An unusual amount of downloads in the system
Malicious activity is something different from typical behavior and activity on an endpoint. And Endpoint protection tool can readily spot this activity through the endpoint behavior analysis tool. ML/AI and EBA are technologies that ensure that malware attack doesn't happen on your endpoint.
How does EDR Detect anomalies?Here is some technique that this software uses to detect malware attacks.
Signature-based DetectionIt is the best technique to spot known malware attacks. Every malware has a specific signature and behavior. EDR keeps a complete database of all this malware. Once it finds a suspicious activity, the system compares the codes with known malware databases. If it finds a match, the system readily isolates the infected endpoint to ensure the attack won't spread in the overall business network.
Behavior Analysis with Machine learningAn Endpoint detection tool is far better than an antivirus because it can detect known and unknown threats. It uses a signature-based detection tool to figure out the file-based attack. But when dealing with unknown threats, it relies on advanced machine learning and behavior analysis techniques.
The endpoint agent keeps track of all the activities and behavior. All the data is stored in a centralized cloud database. Now once the system discovers some anomaly, it starts analyzing it. First, it checks known malware.
If the code doesn't match, it performs further analysis. It is good to know that the behavior of malware and cyber threat always differs from usual activities on your devices.
The Latest technologies like Machine learning and Artificial intelligence empower your team and this tool, enabling you to detect new threats. When handling fileless attacks, Xcitium EDR is designed with advanced capabilities. You can prevent zero-day attacks through this software.
Final Thoughts -What Activates an EDR?
An EDR gets activated by malicious attacks. These days, your organization is exposed to various threats, such as phishing attacks, password attacks, malware,denial-of-Service, crypto-jacking, ransomware, and much more.
According to an IBM study, a Ransomware attack costs $4.54 million.You want to avoid experiencing that much financial loss. Besides, you may experience data loss due to these attacks as well. So, if you want to stay proactive with your endpoint security approach, you need to get this endpoint protection solution. It is a strong defense against cyber attacks of every kind and magnitude.