Cybercriminals always want to exploit vulnerabilities in your business system. It would help if you secured every threat vector, such as cloud workstations, remote devices, endpoints, IoT devices, or any other portal. These days, you find specialized security products for every single threat vector.
You can find Network detection tools, Endpoint detection and response platform, firewalls, and many others. Your team finds it difficult to manage multiple solutions EDR, so opting for a Unified system to manage vulnerabilities is necessary. Let's uncover complete details about this platform below:
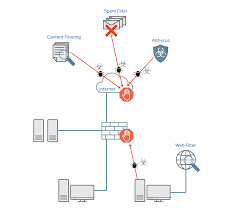
What is a Unified Threat Management Platform?
It is a single platform that combines multiple cybersecurity functions to simplify security visibility and management. Your in-house team doesn't need to switch between standalone products anymore because this one console lets them manage the complete threat landscape efficiently and quickly. Since you no longer rely on multiple platforms and pay for different licenses, it prevents the total ownership cost.
Features of Unified Threat Management Platform
This one portal uncovers the functionalities of different security products. It includes:
Firewall
This network security device filters incoming and outgoing traffic in your organizational network based on pre-defined policies. If it finds any malicious activity or traffic , it becomes the barrier that doesn't let that traffic enter your system.
Site-to-Site and Client-to-Site VPN (Virtual Private Network)
Instead of getting an outside VPN service, your SOC team can rely on a built-in VPN, ensuring a safe and encrypted online connection. It gives you more privacy and anonymity while connecting to public networks or the digital world. Your team can block some IPs based on geographic location.
Identity-Based Security Policies
It allows your team to let only authorized personnel access your business system. It is the most important function of UTM because only authorized personnel will log in when your business is expanded to international borders, or remote users are connected to your system. Besides, you can decide on different levels of access for different users.
URL Filtering
Your organization often experiences an attack because your employee opens an URL by mistake. To prevent such attacks, you should go for URL filtering. It is a procedure where your in-house team will block certain URLs loading on your network. If an employee tries to access it, they will be redirected to a search engine or another page. When you have a malicious URL list, you can block it through this filter.
Application Control
This system is designed to detect the traffic of all applications connected to a network. In case of any suspicious traffic tries to access your IT Infrastructure, it will be readily blocked or eliminated to prevent system-wide attack via an application.
A solid UTM will allow your organization to identify potential threats and uninstall an app before it causes any damage.
Intrusion Prevention System
DDoS attacks are becoming pretty common, and the best way to stop such attacks is through IPS. It will monitor the network if you install hardware in your organization or rely on software. In case of any malicious activity or network, the system will readily block or drop it to prevent a malware attack while sharing a complete report.
Antivirus
It is a program that scans your system files and codes to identify and remove viruses. This program aims to eliminate malware that can damage your computer or laptop.
Many times, a UTM is designed with advanced or next-generation antivirus. This program relies on signature-based detection and behavior-learning tools to spot and stop known and unknown malware attacks on your business system.
Data Loss Prevention
This portal also has DLP that ensures that the data in all storage, transit, or use forms should be well-protected. The system administrator will monitor how users access and use data to prevent data loss or breach.
Centralized Management
The best part about Unified Threat Platform is that you can perform all cybersecurity functions from a single platform. Your team can block a URL or stop an attack from a single pane. Besides, they can easily grasp next-level visibility into the complete ecosystem through this platform. It offers them better control and management of potential threats and vulnerabilities.
Do you need a Unified Threat Management Platform?
If your organization wants to prevent and stop advanced malware attacks on the complete threat landscape, there is a need for a simple cybersecurity approach with the UTM portal. It consolidates all security tools at one point and allows your team to prevent an attack before it leads to zero-day attacks, DDoS, social engineering, or ransomware.
