Similar to Golden Ticket attacks, silver attacks take advantage of Kerberos to exploit its design to compromise credentials; however, unlike Golden Tickets, silver attacks only provide access to one service.
For Silver Ticket attacks, watch for suspicious service ticket requests with an RC4 encryption of type 0x17. Varonis can alert you if hacking tools like Mimikatz appear on your monitored data storage.
A Silver Ticket Attack exploits weaknesses in Kerberos identity authentication protocol to forge ticket-granting service (TGS) tickets, with only those services authorized by TGS being accessible. It's much less wide-reaching than Golden Ticket attacks, as only access services that will be authorized are possible.
To produce a TGS ticket, an attacker needs to gather the password hash of an account on a compromised system and store it securely; this can be accomplished using OS credential dumping attacks such as Mimikatz or brute force using Kerberoasting tools. Once they possess this hash, they can authenticate any service supporting TGS tickets directly without going through KDC; manipulating this ticket could elevate their privileges until Domain Administrator status is achieved.
As an organization, you can protect against such attacks by prohibiting credential dumping, disabling PAC, and mandating that users regularly change their passwords. Furthermore, access can be restricted on systems not to share administrative privileges across security boundaries, and OS features that permit attackers to carry out attack patterns are disabled.
Varonis EDN solutions also feature preventive alerts that can identify attacks as they happen. Varonis gathers and analyzes activity data from Active Directory, the network perimeter, and data storage to detect suspicious activity throughout a kill chain - including lateral movement, privilege escalation, and ticket creation, as seen here. In particular, it can recognize hacking tools like Mimikatz and Kerberoast being used against monitored devices by comparing activity against previous behaviors to generate alerts when anomalies are discovered.
How Silver Ticket Attacks Work
Attackers need access to systems or devices within an enterprise environment (directly or through compromises like phishing attacks, malware downloads, or OS exploits). Once they gain initial access, attackers can use tools like Mimikatz to forge Kerberos tickets and access specific services. Step one is identifying and obtaining a targeted service's Domain Security Identifier and DNS name before gathering its local NTLM hash or password hash for that service. This data can be extracted using OS credential dump or offline cracking (Kerberoasting). Once attackers possess this data, they can use tools to forge Kerberos Ticket Granting Service (TGS) tickets that allow access to that specific target service.
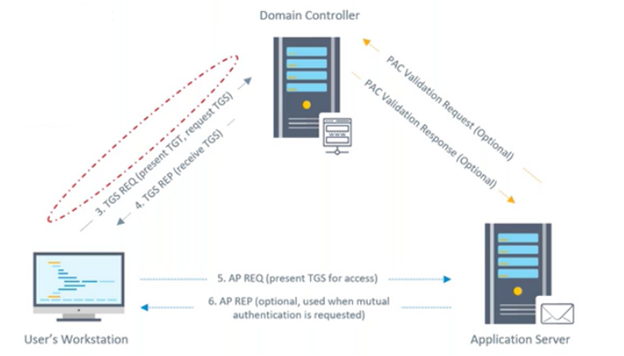
Once an attacker creates a TGS, they can leverage it to move laterally across the network. They bypass most cybersecurity measures, including Privileged Account Management solutions that restrict stolen password usage and MFA solutions that require additional authentication factors before accessing compromised machines.
Silver Ticket attacks can be difficult to detect since they only allow adversaries to forge TGS tickets for specific services. Support for this attack has become standard on most tools, such as Mimikatz, making adoption by low-skill attackers and nation-state groups easier.
Silver Ticket attacks are extremely harmful because they allow attackers to bypass most security measures in an enterprise and gain entry to its networks. By manipulating Active Directory ticketing systems and access systems to forge tickets and gain entry, attackers can bypass most security controls such as Privileged Account Management solutions, MFA solutions; OS exploit mitigation such as Windows ATP locking, or even UEFI BIOS locking solutions.
What Can Attackers Do With a Silver Ticket?
Golden Tickets give attackers access to the entire domain, while Silver Tickets allow only forging ticket-granting service (TGS) tickets on compromised systems. To achieve their objective, attackers must break a password hash from a local computer account's Security Account Manager (SAM) or local service account to create TGS tickets for specific services. Silver Ticket attacks may not be as powerful as Golden Ticket attacks. Still, they have proven useful tools for internal red teams, malicious cyber criminals, and nation-state attack groups. Silver Ticket attacks allow attackers to escalate privileges in targeted environments without engaging the DC, making it harder to detect these attacks than Golden Ticket attacks.
An attacker launching a Silver Ticket attack must first gain control of a system environment through one or more methods, such as phishing campaigns, exploiting vulnerable or misconfigured IT assets, or malware infections. Once inside, an attacker must conduct reconnaissance to gather details like domain name and local security identifier of target services using tools like Mimikatz.
An attacker then creates a TGS ticket using the stolen hash and uses it to authenticate to a service, such as a command prompt. Most services do not verify signatures in TGS tickets and will instead trust it blindly, giving access to more advanced cyberattacks such as lateral movement or data exfiltration.
Varonis allows organizations to recognize suspicious behavior that indicates a Silver Ticket attack is underway and take swift steps to counter this threat. Varonis categorizes all accounts into different types, such as user, service, and privileged accounts, and compares current activity against past behavior of these accounts.
Preventing Silver Ticket Attacks
Silver ticket attacks involve forging Kerberos tickets, which allow attackers to gain privileged access to specific services. While less potent than Golden Tickets attacks, such as exfiltration or ransomware attacks, skilled threat actors still utilize this technique effectively to reach larger goals such as exfiltration and ransomware attacks.
To conduct a Silver Ticket Attack, adversaries must first obtain the NTLM hash for any computer account or service on which they want to operate a Silver Ticket Attack. This may be achieved through OS credential dumping techniques (for example, Mimikatz or Kerberos) or exploiting an endpoint that has been compromised. Once in possession of this hash, attackers can create an invalid ticket-granting service (TGS) ticket to gain privileged access on other domain-joined systems - even impersonating any user with high privileges!
Silver Ticket attacks can be difficult to detect due to their subtle nature; TGS tickets created without communicating with DC are only ever verified through third-party Privileged Account Certificate of service (event 4769),making detection even harder. Furthermore, attackers often do not verify ticket signatures as part of this tactic, further complicating detection efforts.
To guard against silver ticket attacks, an effective cybersecurity defense must exist to detect any anomalous activities and stop their exploitation before it's too late. Implement a least privilege model and restrict administrator access; audit service accounts to ensure passwords aren't reused across the organization; implement strong password policies; and enable privileged attribute certificate validation. Deploying an enterprise data protection solution such as Varonis can further help mitigate cyber attacks by identifying and analyzing all accounts across your network, categorizing them as user, service, or privileged accounts, and alerting you when suspicious activity occurs.
Mitigating and Responding to Silver Ticket Attacks
Silver Ticket attacks take advantage of vulnerabilities in the Kerberos authentication protocol to gain entry to an organization's network without valid credentials or authorization from personnel within it. As such, prevention and response strategies against this threat must be prioritized for businesses to safeguard sensitive data.
Although less dramatic than Golden Ticket attacks, Silver Ticket attacks remain popular with internal "red team" attackers, malicious cyber criminals, and nation-state attack groups due to their low threshold for execution. Furthermore, Mimikatz supports this type of attack as a standard feature, lowering the bar for adversaries looking to execute these attacks.
To protect against this threat, organizations should implement password management software that enforces strict password standards and changes them frequently. They should also ensure that their employees do not use shared computers for work and that individual accounts have unique passwords, making cracking them harder.
Additionally, they should ensure their security settings for Kerberos are configured appropriately, including setting a maximum acceptable life of tickets for users and not exceeding your logon hours. Any settings beyond your initial logon hours could allow users to access network services outside their logon hours while also negatively affecting KDC performance in ticket requests resulting in DoS attacks against it.
Also, they should enable privileged attribute certificate validation for Kerberos to prevent attackers from misusing service tickets that have been falsified to create authenticator tokens that cross security boundaries. By taking these preventive steps and mitigating risks associated with Silver Ticket attacks, organizations can significantly decrease their exposure and safeguard key assets.





