Your company network might be facing a wide range of threats. In order to be prepared for such occurrences, it is essential to go beyond implementing security measures and also focus on educating your Blue Team to effectively handle these instances. This is where you can leverage the capabilities of Red Teaming.
Aside from discovering undisclosed vulnerabilities, the primary advantage of conducting a Red Teaming assessment is helping defenders to experience a realistic malicious event. Let's delve deeper into what red teaming entails and what benefits it can bring to your business.
What Involves Red Teaming?
Red teaming is a comprehensive and structured process that surpasses conventional penetration testing by simulating real-world cyber-attack. It uses replication of actual techniques, tactics, and procedures that adversaries use. Unlike traditional pen testing, a red teaming exercise operates with minimal prior knowledge, ensuring that the organization is not notified in advance and the red team receives no preliminary information. This approach helps businesses identify weaknesses and potential attack vectors that may go unnoticed through traditional security assessments.

During this process, the blue team's job is to protect the organization from infiltration during the simulated attack. Here the red team's role is to simulate an attack on the target organization. The red teaming security is mostly external to the organization, but it can be an internal team too.
This simulating assessment particularly put emphasis on exposing potential risks to the vital data from across the entire organization. So your cyber defenses don't stay limited to a particular collection of assets. It is a thorough examination of the company's dangers and weak points, and it also aims to test internal teams' preparedness for such an incident.
How Does Red Teaming Work?
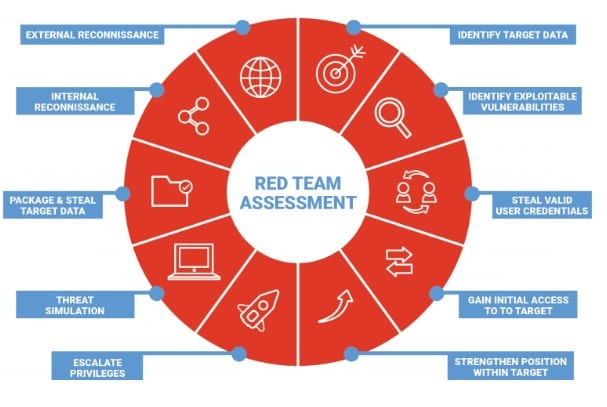
In order to comprehend the specifics of red teaming, is to observe the course of a regular red team practice. Red teaming simulations typically contain multiple stages. Here are the following steps:
Goal Mapping
Red teaming begins with clearly defining the goals and objectives of the exercise. The red team collaborates with the organization to establish specific targets, such as critical systems, sensitive data, or key infrastructure components.
Reconnaissance
During the reconnaissance phase, the red team gathers information about the target organization. This includes researching publicly available data, analyzing online footprints, and identifying potential vulnerabilities or entry points.
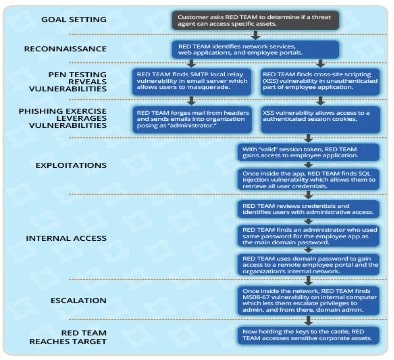
Exploiting Vulnerabilities through Pen Testing And Phishing
Once the reconnaissance is complete, the red team proceeds to exploit vulnerabilities through a combination of penetration testing and phishing attacks. This involves attempting to gain unauthorized access to systems. The assessment will involve exploiting software vulnerabilities or tricking employees into revealing sensitive information through deceptive emails or social engineering tactics.
Internal Access
After successfully penetrating the organization's defenses, the red team works to escalate their privileges and gain deeper access to internal systems and resources. This step simulates an attacker's efforts to move within the network to reach high-value targets.
Escalation
During the escalation phase, the red teaming security focuses on maximizing the impact of their attack as they expand control over critical systems. The attack may involve compromising administrative accounts, manipulating configurations, or accessing sensitive data.
Reaching Target
The assessment ends when the red teaming reaches the designated target. The target can be a specific system, database, or other critical assets. Successfully achieving this goal demonstrates the potential impact of a real-world attack and highlights the areas requiring immediate attention.
Common Tactics And Tools Used In Red Teaming
Red teaming leverages a variety of tactics and tools to simulate real-world attacks. Here are those tactics:
Application Penetration Testing
As the name suggests, it helps to identify vulnerabilities in applications and software through testing. The red teaming assessment involves analyzing the code, performing input validation checks, and attempting to exploit weaknesses to gain unauthorized access or execute malicious code.
Physical Penetration Testing
Physical penetration testing evaluates an organization's physical security controls by attempting to gain unauthorized access to your network infrastructure. This could include bypassing security measures tailgating, or exploiting social engineering techniques to gain entry.
Network Penetration Testing
This identified an organization's network vulnerabilities in the infrastructure. The red team attempts to exploit weaknesses in network devices, misconfigurations, or weak access controls. They would gain unauthorized access or conduct reconnaissance.
Intercepting Communication
Red teams may intercept and analyze communication channels to gain insights into potential weaknesses or sensitive information. This can involve monitoring network traffic, analyzing wireless communications, etc., to gather data.
Social Engineering
Social engineering techniques involve manipulating human psychology to trick employees into divulging sensitive information. Then Social engineering techniques involve manipulating human psychology to trick employees into divulging sensitive information.
How Red Teaming Can Benefit Your Organization?
Red teaming offers several benefits for businesses. Here are some of the ways to access its advantages:
- Identification of risk
- Simulating techniques
- Assessing your organization's security level
- Engagement with internal response teams
- Compliance assistance
- Training and cybersecurity education
- Provide performance-metric Report
Conclusion
Red teaming plays a crucial role in enhancing the security and resilience of businesses in today's evolving cyber threat landscape. Their service and test will assess your cyber defenses against realistic malicious attack situations in an ethical way. Hence, improve the incident response capabilities of your internal teams. If you want assistance with red teaming security, get in touch with Xcitium for any kind of threat detection technological solution.
