What is Purple Teaming?
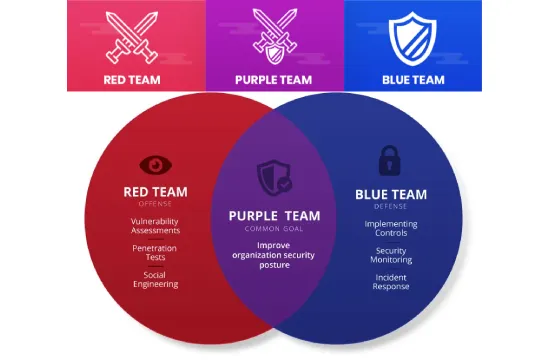
Purple Teaming is a cybersecurity approach that bridges the gap between offensive and defensive security strategies. Traditionally, cybersecurity teams are divided into two groups: Red Teams, which simulate real-world attacks to identify vulnerabilities, and Blue Teams, which focus on defending the organization against these threats. While both teams play a critical role in strengthening security, they often operate in isolation, leading to missed opportunities for learning and improvement. Purple Teaming was developed to address this challenge by fostering collaboration between the two teams.
At its core, Purple Teaming is about improving security posture through continuous testing, communication, and shared insights. Instead of working separately, the Red Team and Blue Team actively engage with each other, exchanging knowledge in real-time to refine attack simulations and enhance defensive capabilities. This collaborative effort allows organizations to detect gaps in their security infrastructure, improve incident response strategies, and develop more effective threat mitigation techniques.
One of the key advantages of Purple Teaming is its ability to create a feedback loop that accelerates learning and adaptation. When Red Team members execute an attack simulation, they share their tactics and methodologies with the Blue Team. This transparency enables defenders to see exactly how adversaries might exploit weaknesses, allowing them to strengthen their defenses accordingly. In return, the Blue Team provides insights into detection and response strategies, helping attackers refine their techniques and make future assessments more realistic. This iterative process ensures that security teams remain agile and proactive in the face of evolving threats.
Another important aspect of Purple Teaming is its focus on measurable outcomes. Organizations implementing this approach often set clear objectives and key performance indicators (KPIs) to track progress. These may include the time it takes for the Blue Team to detect and respond to an attack, the number of vulnerabilities identified and remediated, and improvements in security awareness across the organization. By analyzing these metrics, organizations can continuously refine their security strategies and prioritize areas that require attention.
Purple Teaming is especially valuable in today’s complex cybersecurity landscape, where threats are becoming increasingly sophisticated. By breaking down silos between offensive and defensive teams, organizations can create a more resilient security framework that adapts to emerging risks. Whether performed in-house or with the help of external cybersecurity experts, Purple Teaming provides a structured and effective way to strengthen an organization’s ability to detect, prevent, and respond to cyber threats.
How Purple Teaming Differs from Red and Blue Teaming
Purple Teaming differs from Red and Blue Teaming by integrating the strengths of both offensive and defensive security strategies into a collaborative approach. Traditionally, cybersecurity operations are divided between the Red Team, responsible for simulating real-world cyberattacks, and the Blue Team, tasked with defending against those attacks. While both teams serve critical functions, they often operate independently, limiting the effectiveness of security improvements. Purple Teaming bridges this gap by facilitating direct collaboration between the two teams, ensuring a continuous feedback loop that enhances an organization’s overall security posture.
Red Teaming focuses on offensive security by emulating the tactics, techniques, and procedures (TTPs) of real-world attackers. The goal is to uncover vulnerabilities before malicious actors can exploit them. Red Team exercises involve penetration testing, social engineering, and adversary simulation to challenge an organization’s defenses. However, since Red Teams typically work in isolation, their findings may not always translate into actionable improvements for the Blue Team, especially if there is a lack of communication or coordination.
Blue Teaming, on the other hand, prioritizes defensive security, ensuring that the organization has effective monitoring, detection, and response mechanisms in place. Blue Teams leverage security tools such as SIEM (Security Information and Event Management) systems, endpoint detection and response (EDR) solutions, and network monitoring to identify and mitigate cyber threats. The challenge with Blue Teaming alone is that it often relies on predefined security policies and historical attack patterns, making it harder to anticipate novel threats or sophisticated attack techniques that Red Teams might uncover.
Purple Teaming combines both approaches, fostering a collaborative environment where the Red Team and Blue Team share real-time insights, methodologies, and strategies. Instead of working in silos, these teams actively communicate to enhance both offensive and defensive capabilities. Red Teams provide direct feedback to Blue Teams on how attacks are executed, while Blue Teams use this information to fine-tune their detection and response strategies. This process not only accelerates learning but also ensures that security gaps are addressed more efficiently.
Unlike traditional Red and Blue Team exercises, which can sometimes be adversarial, Purple Teaming is a cooperative process that prioritizes security improvement over competition. By focusing on continuous assessment and adaptation, organizations using Purple Teaming can stay ahead of evolving threats. This approach creates a more resilient security posture, as both teams actively refine their tactics to better detect, prevent, and respond to cyber threats in real-world scenarios.
Why is Purple Teaming Important in Cybersecurity?
Purple Teaming is crucial in cybersecurity because it fosters a collaborative approach that enhances both attack simulation and defense mechanisms, making organizations more resilient against evolving threats. Traditional cybersecurity strategies often rely on the separate functions of Red Teams, which simulate attacks, and Blue Teams, which defend against them. However, when these teams operate in isolation, organizations miss opportunities to strengthen their security posture effectively. Purple Teaming bridges this gap by encouraging real-time collaboration, ensuring that security weaknesses are identified and addressed more efficiently.
One of the primary reasons Purple Teaming is important is that it helps organizations stay ahead of increasingly sophisticated cyber threats. Attackers continuously develop new tactics, techniques, and procedures (TTPs) to bypass security measures, making it essential for defenders to evolve just as quickly. By integrating offensive and defensive strategies through Purple Teaming, organizations can anticipate potential attack vectors, simulate realistic threats, and refine their security controls to detect and mitigate risks proactively.
Another key benefit of Purple Teaming is the creation of a continuous feedback loop between attackers and defenders. In a traditional security model, Red Teams conduct penetration tests or adversary simulations and provide reports on discovered vulnerabilities. However, without direct collaboration, Blue Teams may struggle to interpret findings or implement necessary improvements effectively. Purple Teaming eliminates this disconnect by enabling real-time communication and shared learning, allowing security teams to immediately apply insights from simulated attacks to strengthen their defenses.
Purple Teaming also improves incident detection and response. Many security breaches occur because Blue Teams rely on pre-defined security measures and threat intelligence that may not fully account for emerging attack techniques. With a Purple Teaming approach, security teams can fine-tune their detection and response strategies based on actual adversary behavior rather than theoretical models. This enhances the organization’s ability to recognize threats quickly and respond effectively, reducing the potential impact of cyberattacks.
Additionally, Purple Teaming increases the return on investment (ROI) in cybersecurity programs. Many organizations invest heavily in security tools and infrastructure, but without effective testing and validation, these defenses may not perform as expected under real attack conditions. Purple Teaming ensures that security investments are continuously assessed and optimized, maximizing their effectiveness in protecting critical assets.
As cyber threats continue to grow in complexity, Purple Teaming has become an essential practice for organizations looking to strengthen their security posture. By fostering a culture of collaboration and continuous improvement, Purple Teaming empowers security teams to detect, prevent, and respond to threats more effectively, ultimately reducing the risk of successful cyberattacks.