Pretexting is the implementation of a false story or pretext to gain the trust of a target and then manipulate or fool them into disclosing personal information, downloading malicious software, sending money to criminals, or hurting themselves or the business they work for.
Pretexting is an important strategy in targeted social engineering attacks such as whaling, spear phishing, and business email compromise (BEC). However, both traditional criminals and cybercriminals have been known to use pretexting to steal valuable data or assets from people or businesses.
How pretexting works?
Security specialists argue that most pretexts are made up of two main components: a character and a situation. The scammer's character is the role he or she performs in the plot. To establish credibility with the potential victim, the scammer usually impersonates someone in authority over the victim, such as a boss or executive, or a person the victim is likely to trust, such as a coworker, IT employee, or service provider. Some attackers may attempt to imitate the friends or loved ones of a targeted victim.
The circumstance is the plot of the scammer's fabricated story—the reason why the character is requesting something from the victim. Situations can be broad (for example, 'you need to update your account information') or quite detailed, especially if the scammers are targeting a specific victim. Threat actors often conduct web research on their characters and targets in order to make their character impersonations and scenarios credible. It is not difficult to accomplish. According to one investigation, with just 100 minutes of basic Google, hackers may create a compelling story based on information from social media feeds and other public sources.
Spoofing the character's email address or phone number or acquiring outright unauthorized access to the character's actual email account or phone number and using it to deliver the message are other strategies for making characters more credible. In what could be a foreshadowing of the future of pretexting, in 2019, scammers duped a U.K. energy firm out of USD 243,000 by impersonating the voice of the CEO of the firm's parent company and making bogus phone calls asking for payments to the firm's suppliers.
Pretexting and other social engineering types
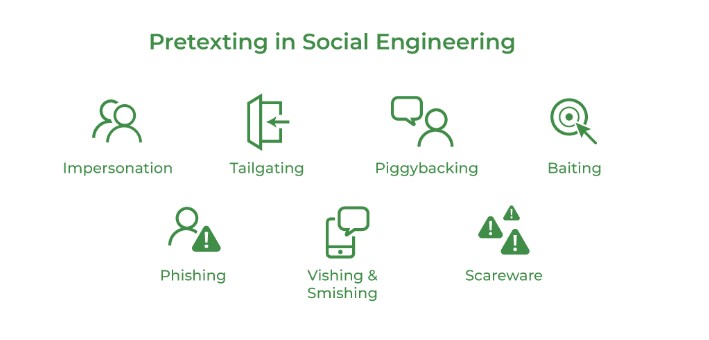
A lot of social engineering scams rely on pretexting, including:
Phishing
Pretexting is especially common in targeted phishing attacks, such as spear phishing (a phishing attack that targets a specific individual) and whaling (a spear phishing attack that targets an executive or a staff member with privileged access to sensitive information or systems).
Tailgating
Tailgating, sometimes known as "piggybacking," is when an unauthorized person enters a space that needs clearance, like a secure office building, by following an authorized person. Pretexting is a technique used by con artists to boost the success of their phishing attacks. One example is pretending to be a delivery person and requesting an unwary employee to open a locked door for them.
Baiting
In these attacks, a criminal dupes victims into downloading malware by luring them with enticing but harmful bait The bait could be digital (for example, promotions for free downloads of movies that turn out to be malware) or physical (for example, USB sticks that have been loaded with malicious code and left in public places). Pretexting is often used by scammers to make the bait more appealing. A scammer, for example, might add labels to a compromised USB stick to make it appear to belong to a specific organization and contain sensitive files.
How to Prevent Pretexting?
DMARC
Impersonation is a part of pretexting, and for it to work, the email needs to seem authentic. As a result, email spoofing is required. The most common kind of email spoofing prevention, Domain-based Message Authentication, Reporting, and Conformance (DMARC), is limited since it requires ongoing and complex maintenance. Additionally, while spear-phishing attacks use name or cousin domain spoofing much more continuously, DMARC only recognizes exact domain spoofing.
AI-Based Email Analysis
Enterprises must work towards a more modern detection strategy than DMARC to prevent pretexting. Next-generation anti-spear phishing technology analyses user behavior to spot pretextual cues using artificial intelligence (AI). It can also detect irregularities in email addresses and email traffic, such as cousin domains and display name spoofing. The field of artificial intelligence known as "Natural Language Processing" (NLP) examines language and has the ability to decipher words and phrases used in spear-phishing and pretexting.
User Education
Finally, help your users learn how to spot pretexting by giving them examples from everyday life. Because users are frequently unaware of the aforementioned pretexting techniques and cannot discern anything unusual about the requests they receive, spear-phishing and pretexting frequently succeed. Users should be made aware of the various forms of email spoofing and instructed on how to spot cousin domains and display name spoofing in email addresses. You must also have standards in place for financial transactions, such as confirming requests in person or over the phone.
Conclusion - How Xcitium can help?
Pretexting is when an attacker creates a false identity in order to trick their victims into disclosing personal information. Active advanced threats can be detected by Xcitium EDR security detection. Learn how Endpoint Detection Response (EDR) works to secure company data. Visit for more.
FAQ section
A: While technology can help identify phishing emails and malicious links, pretexting relies on human manipulation, making it difficult for technology alone to detect such attacks.
A: Pretexting can be illegal when it involves deception, fraud, or violates privacy laws. Laws regarding pretexting may vary in different jurisdictions.
A: If you suspect a pretexting attempt, refrain from sharing information, report the incident to your organization's security team, and follow their guidance.
A: While it's challenging to prevent all pretexting attacks, awareness, education, and implementing security measures can significantly reduce the risk.