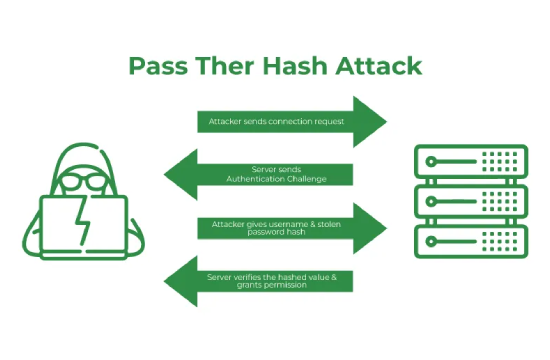
What is a Pass-the-Hash Attack (PtH)?
A Pass-the-Hash (PtH) attack is a cybersecurity exploit in which an attacker steals hashed credentials from a compromised system and uses them to authenticate as the original user without needing to crack or recover the actual password. This technique is particularly dangerous because it bypasses traditional authentication mechanisms and allows lateral movement within a network, often leading to privilege escalation and widespread system compromise.
PtH attacks target authentication protocols that rely on password hashes, such as NTLM (NT LAN Manager) and Kerberos in Windows environments. When a user logs into a system, their password is typically converted into a hash, a cryptographic representation that is stored in memory. Attackers who gain access to a system can extract these stored hashes and reuse them to authenticate on other systems without needing to decrypt the original password. Since many organizations use the same credentials across multiple systems, a successful PtH attack can allow threat actors to navigate an entire network with minimal resistance.
The attack process typically begins with the attacker obtaining initial access to a system, often through phishing, malware, or exploiting unpatched vulnerabilities. Once inside, they use tools such as Mimikatz, Metasploit, or Windows Credential Editor to extract password hashes from memory or system files. These hashes are then "passed" to another system, effectively granting the attacker access as if they had entered the correct password. This allows them to move laterally through the network, access sensitive data, install backdoors, and escalate privileges to gain control over critical infrastructure.
One of the reasons PtH attacks are so effective is that they exploit weaknesses in credential management and authentication practices. Many organizations rely on password-based authentication without additional security layers such as multi-factor authentication (MFA) or endpoint detection and response (EDR) solutions. Additionally, users often have administrative privileges on multiple systems, meaning that compromising a single set of credentials can open access to an entire network.
To defend against Pass-the-Hash attacks, organizations should implement security best practices such as enforcing least privilege access, using MFA wherever possible, applying strict credential hygiene policies, and regularly patching vulnerabilities that could be exploited for initial access. Additionally, deploying security solutions that detect abnormal authentication behaviors and unauthorized credential usage can help mitigate the risk of a PtH attack.
Understanding how PtH attacks work and taking proactive security measures is essential for organizations to protect their networks from credential theft and unauthorized access. By implementing a layered security approach, businesses can significantly reduce the likelihood of successful PtH exploits and strengthen their overall cybersecurity posture.
Common Targets of Pass-the-Hash Attacks
Pass-the-Hash (PtH) attacks can target a wide range of systems and users, but certain environments and account types are more vulnerable than others. Attackers typically focus on systems where password hashes are stored in memory, allowing them to extract and reuse credentials without decrypting the original password. Understanding the common targets of PtH attacks is crucial for organizations looking to strengthen their defenses against this pervasive threat.
One of the primary targets of PtH attacks is privileged accounts, such as domain administrators and system administrators. These accounts have elevated permissions that grant access to critical systems, sensitive data, and network configurations. If an attacker successfully compromises a privileged account through a PtH attack, they can gain full control over the network, deploy ransomware, exfiltrate data, or even create backdoors for persistent access. Since privileged accounts often have broad access across multiple systems, they provide an ideal pathway for lateral movement and privilege escalation.
Another key target is workstations and endpoints used by IT personnel. IT administrators frequently access multiple systems and servers, often using remote desktop sessions or command-line interfaces that store hashed credentials in memory. If an attacker gains access to an IT administrator’s workstation, they can extract and pass the hash of an admin account to gain higher privileges. Additionally, developers and engineers with access to production environments are attractive targets due to their ability to modify code and infrastructure settings.
Windows-based enterprise environments are particularly vulnerable to PtH attacks due to their reliance on authentication protocols like NTLM and Kerberos. While Microsoft has introduced security measures to mitigate PtH attacks, many organizations still use legacy authentication methods that store password hashes in memory, making them easy targets. Attackers can exploit vulnerabilities in domain controllers, Active Directory, and shared resources to move laterally across an enterprise network.
Remote and unmanaged systems are also high-priority targets. Employees who connect to corporate networks using personal or unmanaged devices may not have adequate security controls, making them easier to compromise. Attackers can extract password hashes from these endpoints and use them to gain access to internal systems. Similarly, virtual private networks (VPNs) and remote desktop protocol (RDP) sessions can be exploited if credentials are stored insecurely.
Third-party vendors and contractors with network access pose another risk. Many organizations provide external partners with credentials to access internal systems, but if these credentials are compromised, attackers can use PtH techniques to infiltrate the network. Because third-party security practices are often outside an organization’s control, they present a significant vulnerability.
Understanding these common targets allows organizations to implement proactive security measures, such as enforcing least privilege access, monitoring authentication behaviors, and using multi-factor authentication to reduce the risk of PtH attacks. By securing high-value targets, businesses can significantly limit the damage that an attacker could inflict through credential theft and unauthorized access.
How Zero Trust Security Helps Prevent PtH Exploits
Zero Trust Security is a modern cybersecurity framework designed to prevent unauthorized access by eliminating implicit trust in users, devices, and network traffic. Since Pass-the-Hash (PtH) attacks exploit the reuse of hashed credentials to gain unauthorized access, Zero Trust principles provide an effective defense against this type of threat. By enforcing strict identity verification, continuous monitoring, and least privilege access, organizations can significantly reduce their exposure to PtH exploits.
One of the core tenets of Zero Trust is identity verification and strong authentication. Traditional authentication methods rely on passwords and hashes, which attackers can steal and reuse in PtH attacks. Zero Trust security mitigates this risk by implementing multi-factor authentication (MFA), which requires users to provide additional verification factors, such as biometric authentication or one-time passcodes, before gaining access. This prevents attackers from using stolen hashes alone to authenticate into systems.
Another key aspect of Zero Trust is least privilege access control. In many PtH attacks, attackers exploit users with excessive permissions to move laterally across a network. Zero Trust enforces role-based access control (RBAC) and just-in-time (JIT) access to ensure users only have access to the resources they need for a limited time. By restricting unnecessary administrative privileges, organizations can limit an attacker's ability to escalate privileges using stolen credentials.
Continuous monitoring and anomaly detection are also fundamental components of Zero Trust security. Unlike traditional security models that only verify identity at login, Zero Trust continuously analyzes user behavior and system activity to detect unusual patterns. If an attacker attempts to use a stolen hash to access a system, security tools such as user and entity behavior analytics (UEBA) and security information and event management (SIEM) solutions can detect suspicious authentication attempts and flag them for investigation. This proactive approach helps stop PtH attacks before they cause significant damage.
Zero Trust also eliminates reliance on static passwords and stored hashes by adopting passwordless authentication methods, such as cryptographic keys or identity-based certificates. These authentication techniques prevent attackers from extracting usable credentials from system memory, closing one of the primary attack vectors for PtH exploits.
Finally, network segmentation and microsegmentation play a critical role in preventing lateral movement. Even if an attacker gains initial access to a system, Zero Trust ensures that access to other parts of the network requires additional verification and monitoring. By isolating sensitive systems and restricting lateral movement, organizations can prevent PtH attacks from spreading and causing widespread damage.
Implementing Zero Trust security provides a comprehensive defense against PtH exploits by requiring strict identity verification, reducing reliance on reusable credentials, and continuously monitoring for suspicious behavior. Organizations that adopt a Zero Trust model can significantly strengthen their security posture and mitigate the risks posed by advanced credential-based attacks like Pass-the-Hash.