What is Password Spraying?
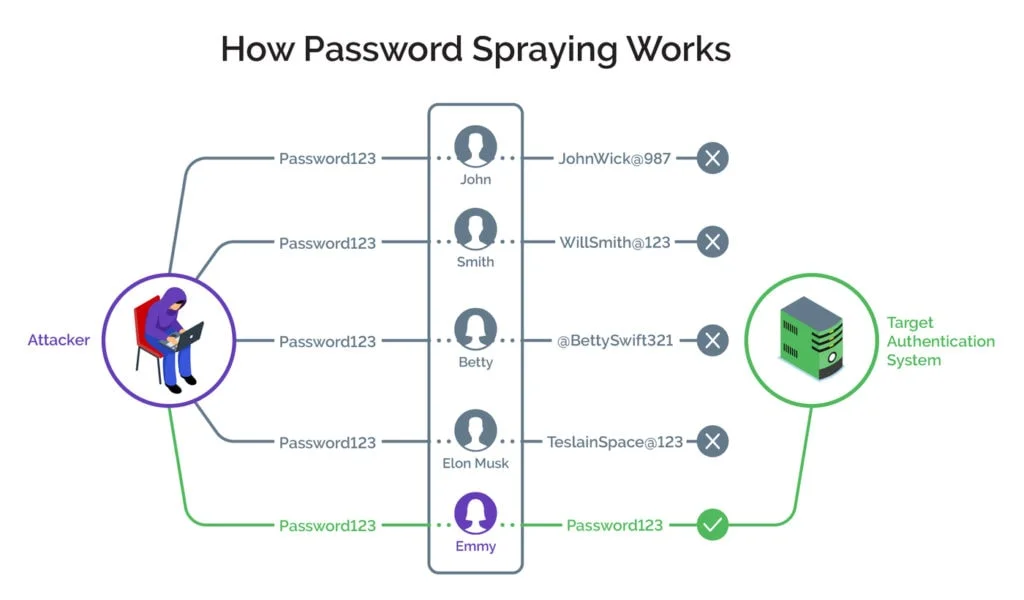
Password spraying is a type of cyberattack that systematically tests a single common password across many accounts before moving on to another password. Unlike traditional brute force attacks that attempt to guess multiple passwords for a single account, password spraying takes a more strategic approach by spreading out attempts to avoid triggering account lockout mechanisms. This method allows attackers to remain undetected while systematically compromising user credentials.
Attackers use password spraying to exploit weak password policies and common user behaviors. Many users tend to choose weak and predictable passwords, such as “password123,” “qwerty,” or “letmein.” Since organizations often enforce account lockouts after a few failed login attempts on a single account, hackers avoid drawing attention by limiting the number of attempts per account. Instead, they test a commonly used password across a large number of accounts within an organization or service, minimizing the risk of triggering security alerts.
One reason password spraying is so effective is that many organizations still rely on outdated password policies. Employees and users frequently reuse passwords across multiple platforms, and some companies enforce periodic password resets without requiring unique, strong passwords. This results in a high probability that at least some accounts within a given system use weak or default passwords that attackers can easily guess.
Password spraying attacks typically target cloud-based applications, enterprise login portals, and remote access services such as VPNs and single sign-on (SSO) platforms. These services are particularly vulnerable because they are exposed to the internet, allowing attackers to attempt logins from anywhere in the world. Microsoft 365, Google Workspace, and other widely used business applications are common targets for password spraying attacks due to their widespread adoption.
Detecting password spraying attacks can be challenging because they often blend in with normal login activity. Security teams must monitor for abnormal login patterns, such as multiple failed authentication attempts across different accounts from a single IP address or logins from unexpected geographic locations. Implementing multi-factor authentication (MFA) is one of the most effective ways to prevent password spraying attacks, as it adds an additional layer of security beyond just a username and password.
Organizations can also defend against password spraying by enforcing strong password policies, educating users on secure password practices, and using tools like behavioral analytics to detect unusual login attempts. Regular audits of user credentials and proactive security monitoring can help mitigate the risk of password spraying and other credential-based attacks.
Comon Targets of Password Spraying Attacks
Password spraying attacks target a wide range of organizations and individuals, but certain sectors and types of accounts are particularly vulnerable due to their security practices, accessibility, and the value of the data they protect. Attackers typically focus on accounts that provide access to sensitive information, financial resources, or critical infrastructure. Understanding the common targets of password spraying can help organizations implement stronger defenses and reduce the risk of compromise.
One of the primary targets of password spraying attacks is cloud-based services and enterprise login portals. Platforms such as Microsoft 365, Google Workspace, and single sign-on (SSO) solutions are popular attack vectors because they often serve as the entry point for corporate networks. Since these services are accessible from anywhere with an internet connection, attackers can attempt to gain unauthorized access without needing physical proximity to the target organization.
Government agencies and critical infrastructure providers are also frequent targets of password spraying attacks. Cybercriminals and nation-state hackers seek access to sensitive government data, classified communications, and critical systems that could be exploited for espionage or sabotage. Agencies that manage law enforcement, national security, energy grids, and transportation systems are particularly attractive targets due to the potential for widespread disruption if their systems are compromised.
Healthcare organizations, including hospitals, medical research facilities, and insurance companies, are another major target. These entities store large amounts of sensitive patient data, including personal health records, insurance details, and payment information. Cybercriminals can use stolen credentials to access patient records for identity theft, insurance fraud, or even ransomware attacks that disrupt medical services.
Financial institutions, such as banks, credit unions, and investment firms, are also heavily targeted by password spraying. Attackers aim to compromise customer accounts, gain access to financial transactions, or even infiltrate internal banking systems. Given the high value of financial data and the potential for fraudulent transactions, these organizations must implement strong security measures to prevent credential-based attacks.
Educational institutions, including universities and research centers, are frequently attacked due to their large user bases and often weaker security policies. Students, faculty, and staff members may use weak passwords, and many institutions lack strong authentication mechanisms. Additionally, research institutions may house valuable intellectual property and sensitive research data that make them appealing targets.
Retail and e-commerce platforms are another common focus of password spraying attacks. Cybercriminals attempt to compromise customer accounts to steal payment information, personal details, and loyalty rewards. Retailers that offer online account access with stored payment methods are particularly at risk, as attackers can quickly make fraudulent purchases if they gain control of an account.
Social media platforms and email accounts are often targeted because they contain personal data, private messages, and linked accounts that can be exploited for further attacks. Once an attacker gains access to a social media or email account, they can use it to launch phishing campaigns, impersonate the victim, or reset passwords for other linked services.
In addition to these major targets, any organization with an online authentication system that does not enforce strong password policies or multi-factor authentication is at risk. Businesses of all sizes, from small startups to large enterprises, must remain vigilant and adopt security best practices to protect against password spraying attacks.
Password Spraying vs Brute Force Attacks
Password spraying and brute force attacks are both credential-based attack methods used by cybercriminals to gain unauthorized access to user accounts, but they differ significantly in their approach, effectiveness, and detection risks. Understanding the distinctions between these attack types can help organizations and individuals implement better security measures to defend against them.
A brute force attack involves systematically guessing passwords for a single user account by rapidly cycling through all possible password combinations until the correct one is found. Attackers typically use automated tools that generate and test thousands or even millions of password variations within a short period. This method relies on sheer computational power and is highly effective against accounts that use weak, short, or easily guessable passwords. However, most modern authentication systems include security measures such as account lockouts, rate limiting, or CAPTCHA challenges that can quickly detect and block brute force attempts.
In contrast, password spraying takes a different approach by testing a small number of commonly used passwords across many different user accounts instead of focusing on a single target. This method allows attackers to bypass account lockout policies, which often trigger only after multiple failed login attempts on a single account. By spreading login attempts across multiple accounts and limiting the number of password guesses per account, attackers can remain undetected while systematically probing for vulnerable credentials.
Password spraying is particularly effective against organizations where employees or users frequently reuse weak passwords. Many users choose simple, easy-to-remember passwords like "123456," "password," or "qwerty," making it easier for attackers to gain access without needing advanced hacking techniques. Since password spraying attacks typically use publicly available credential lists or commonly known passwords, they do not rely on computational power as brute force attacks do. Instead, they exploit human behavior and weak password hygiene.
Another key difference is the speed and stealth of each attack type. Brute force attacks are noisy and generate a high volume of failed login attempts, making them easier to detect through security monitoring tools. Password spraying, on the other hand, is a low-and-slow attack that carefully evades detection by limiting the number of failed attempts per account. Attackers may even use different IP addresses, botnets, or proxy servers to further disguise their activities.
Organizations can defend against both attack types by implementing strong authentication measures such as multi-factor authentication (MFA),which adds an extra layer of security beyond just a password. Enforcing complex password policies, using password managers, and regularly monitoring login activity for unusual patterns can also help reduce the risk of credential-based attacks.
While brute force attacks rely on computing power and sheer volume, password spraying exploits user behavior and weak security policies. Both attacks highlight the importance of strong password management, multi-factor authentication, and proactive cybersecurity strategies to safeguard sensitive accounts and data.