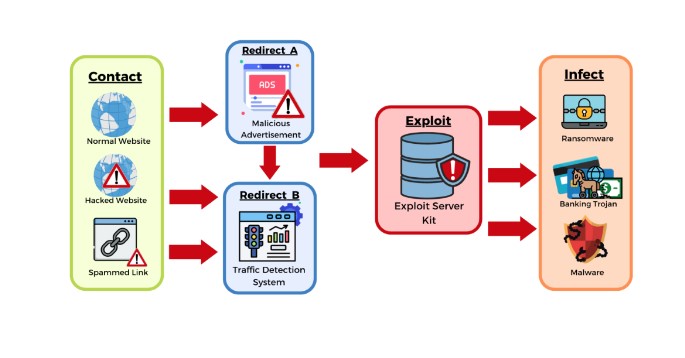
Exploit Kits are used by cybercriminals as the central mechanism in large-scale drive-by download attacks. When an exploit kit lands on an individual device, it quickly begins probing for vulnerabilities before silently installing malware (often ransomware) without their knowledge or consent.
Some exploit kits target zero-day vulnerabilities, while most attack vulnerabilities for which patches exist. Staying current with system software updates is key in lowering the odds that an exploit kit is successful.
Magnitude EK
Cybercriminals utilize exploit kits to spread malware worldwide, infecting users with password-stealing or ransomware. While patches have been released for some of these vulnerabilities, exploit kits remain an effective means of spreading infection.
Exploit kits present a growing threat to online security and are constantly adapting. While they are most frequently employed to distribute ransomware, other malicious attacks have also been launched using exploit kits - for instance, Sundown EK has recently been used to deliver Facestealer malware and Magnitude EK has been found spreading the Magniber ransomware since 2013.
These exploits target Microsoft Windows operating systems and web browsers, Adobe Flash Player, Java, as well as other forms of software like RenderForm. The attackers behind Sundown and Magnitude exploit kits regularly update their arsenal. For instance, recent versions include exploiting vulnerabilities in Microsoft's Flash Player, which is well known yet using various techniques to conceal it from detection.
Magnitude EK kit first surfaced on underground forums for sale in 2013, quickly becoming one of the most widely-used exploit kits to spread malware. According to cybersecurity experts, its primary target area has become the Asia Pacific region, where ransomware spread through malvertising is being spread.
Avast researchers discovered that the Magnitude EK kit contains two new exploits. One takes advantage of an exploit in Google Chrome. In contrast, the other exploits a Windows memory corruption vulnerability - these vulnerabilities allow attackers to circumvent Chrome sandbox and gain system privileges more easily.
Once exploits have been launched, attackers attempt to access the user's browser data and connect with the Command and Control (C&C) server before downloading their final payload, which usually contains ransomware or banking trojan.
At the same time, it is essential to remember that even though these exploits may be outdated, they remain effective because many users ignore or delay software updates. One effective method for protecting yourself against exploits is installing an internet security solution with an anti-exploit feature, blocking harmful ads and stopping malicious downloads. Regular software updates, as well as data backup, will also help safeguard you against these threats.
Nuclear EK
Nuclear EK, one of the oldest exploit kits, has long evaded security analysts' radar. But as revealed by the Cisco Talos Threat Research team's blog post on this exploit kit's success in targeting and exploiting users worldwide - with most attacks coming from Spain alone; nonetheless, it has also been seen in over 10,000 cities worldwide and 150 countries.
Although Angler and Nuclear are no longer present, attackers have not stopped their activity. According to Heimdal Security experts, an increase in Neutrino and RIG exploit kits has been observed - this exploit kit specifically targeted victims who hadn't updated Adobe Flash software patches.
Experts estimate that these two kits have amassed a considerable share of malware traffic due to their sophisticated evasion techniques, which enable them to bypass most signature-based and behavioral/heuristic antiviral solutions and exploits that steal sensitive information from victims' devices.
Nuclear EK's authors continuously revamp their code to expand its attack capabilities, such as providing individual target Flash Player exploits without detection and employing effective obfuscation techniques that prevent malware analysts from tracing infection chains.
As exploit kits become increasingly prevalent, security industry stakeholders must join forces to combat criminal activities associated with exploit kits. Beyond improving AV products, the industry must share threat intelligence and cooperate with law enforcement authorities to combat these criminal acts.
Exploit kits have become a key factor in ransomware infections. Cybercriminals use these tools to deliver CryptXXX ransomware and various malware threats. According to Trustwave's recent report on exploit kits' distribution methods, malvertisements, and social media, campaigns are the two primary methods; attackers frequently use social media campaigns due to their ability to reach larger audiences.
Fallout EK
Exploit kits pose an ongoing threat to organizations. While the threat landscape has changed with the departure of older exploit kits strains like RIG and Nuclear, new variants continue to be developed and deployed against systems software vulnerabilities and popular browser plugins like Adobe Flash Player.
Cybercriminals often employ exploit kits as part of their malware infections to generate income, whether by encrypting files with ransomware, mining cryptocurrency with victim systems' resources, or stealing sensitive information. Attackers have used exploit kits to take advantage of newer features or avoid detection by anti-virus programs - and their attacks continue.
Fallout EK's latest iteration has been detected in malvertising campaigns distributing GandCrab ransomware. This EK employs fingerprinting technology to identify targets of interest before redirecting victims via multiple 302 redirects from legitimate advertiser pages to an exploit kit landing page URL, where payloads vary based on the campaign.
One recent campaign has been linked with the DanaBot banking trojan and Nocturnal info-stealing malware; another campaign targets Microsoft Windows through an RCE vulnerability in VBScript (CVE-2018-8174) to distribute GlobeImposter ransomware; additionally, its exploit kit features modules for DDoS attacks, data extraction, and monetization attacks.
Exploit kits have become widely available as SaaS offerings through underground hacker forums to attackers with limited technical experience. They provide low entry costs, ease of use, and the ability to target specific vulnerabilities, making them attractive options for many criminals. Furthermore, exploit-kit-as-a-service models allow attackers to clone existing versions and add their malicious extensions - providing even those without technical know-how with the means to conduct attacks with limited technical know-how advantage in attacking systems.
Shutting down exploit kits is beneficial. Cybercriminals will likely develop their own and deploy them to monetize malware infections - potentially including exploring different methods for delivering and attacking devices.
To effectively address these threats, organizations must ensure their systems remain current with vendor-recommended patches and updates, retire legacy systems that utilize vulnerable browser plugins such as Adobe Flash Player and use network segmentation techniques to reduce exposure to external attack surfaces.
RIG EK
RIG Exploit Kit is a widely known exploit kit designed to exploit vulnerable web browsers. This exploit kit has been known to distribute ransomware, cryptocurrency miners, spam bots, and banking trojans through malvertisements or compromised websites and has even targeted specific countries or regions since 2014. RIG has been around since 2014 despite numerous takedown efforts but continues to make comebacks.
Exploit chains begin when an actor compromises a website and introduces a malicious iframe, which fetches content from an exploit kit gate and delivers payloads appropriate for their victim machine - such as ransomware, banking trojans, or RATs depending on what goals are set by EK operators for that machine.
This was accomplished using multiple layers of obfuscation by employing various forms of injection: iFrame injection, Base64 encoded strings, and random key to bypass security products from being able to detect it. Furthermore, attackers often changed gate URL patterns to evade detection; RSA research has successfully taken down multiple shadow domains related to this kit.
Once the malicious iframe is executed, its execution leads to redirection to a RIG Exploit Kit landing page where attackers can monitor all aspects of a victim's PC, including IP address, network settings, and installed programs to determine what payload to deploy to them.
RIG has recently taken advantage of vulnerabilities to infiltrate victims with ransomware such as SmokeLoader, and PureCrypter ZLoader IcedID Ursnif. Additional notable malware families distributed include Dridex Raccoon Stealer.
A RIG exploit kit is still making inroads into infections, but there are signs it may be slowing down. Notable among them is an annual decrease in infections as attacks shift more toward crypto miners and info stealers than ransomware attacks - meaning RIG activity hasn't been as substantial since early 2018; nonetheless, its presence remains an essential consideration when assessing your protections against drive-by downloads and exploit kits.
