The latest 2022 Report of Ponemon Institute is quite alarming for businesses. According to this report:
Regarding the frequency of cyber attacks, almost 66 percent of businesses reported it in the past 12 months.
More than 40 percent of businesses claimed that their processes are ineffective in mitigating the risk of cyber-attacks and endpoint threat analysis.
Almost 69 percent believed that cyber- Endpoint threat analysis attacks are becoming quite targeted.
Cybercriminals target attacks on some specific industries more than others. The following are the most vulnerable industries:
• Healthcare institutions
• Corporations
• Banks
• Financial Institutions
• Higher Education
• Accommodation
• Manufacturing
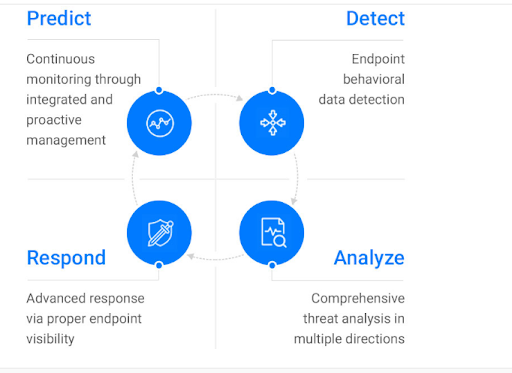
To deal with this exponential level of cyber attacks, businesses must be proactive about their IT infrastructure. And it's where endpoint threat analysis becomes more than essential. It's Endpoint threat analysis time to know what it is and how it helps businesses to keep their Endpoint threat analysis secure and foolproof against cyber criminals' attacks.
What is Endpoint Threat Analysis?
It is a process in which software collects data from the Endpoint threat analysis such as computers, laptops, tablets, phones, and other devices. Data is collected and analyzed in real-time. Every endpoint connecting to your business network is adequately investigated.
During this analysis, security analysis checks the data and tries to identify malicious actors or activities that may attempt to gain access to your Endpoint threat analysis system or hijack your confidential data and information.
An Endpoint Threat Analysis software such as EDR is also used to monitor user activity in the network. So, if there is an Endpoint threat analysis of any suspicious behavior or malicious activity by any user, Endpoint Detection and Response software can identify its reading.
This deep Endpoint Threat Analysis of data, network, and activities makes it easy for businesses to spot any potential threat readily. Endpoint Threat Analysis becomes easy for a security analyst to prevent an attack from happening and try to eradicate suspicious activity before it turns into a severe problem.
How Does Endpoint Threat Analysis Secure Business IT Networks?
Today, every business's network is accessed by remote employees and Endpoint Threat Analysis networks.
According to the Gallup Survey of June 2022, 8 in 10, people are working remotely or hybrid, while only 2 in 10 people are entirely working on-site. This trend of remote working will be around for a while.
Your remote workers can access your confidential business data and information remotely from any endpoint. And it would help if you secured every vulnerable endpoint to prevent cyber attacks.
With the mean of an Endpoint threat analysis tool, your business can get the following benefits:
-
Detect Threats Quickly
An Endpoint Threat Analysis and response software can detect and identify Threats immediately. Cybercriminals can't hide the attack inside your system as EDR monitors your business 24/7. You can identify weak points of your system and make them strong before a criminal exploits them.
-
Deep Insight into Attack
This Endpoint Threat Analysis tool is effective in getting an idea about the origin of cyber attacks. You can easily find out what endpoint is Endpoint Threat Analysis is under attack and how a criminal enters your network. Endpoint Threat Analysis becomes simple to know who is behind an attack. This kind of information through endpoint threat analysis help organization respond to a threat more effectively than before.
-
Preparedness
Thanks to valuable intelligence about the potential attack and Threat, your cyber Endpoint Threat Analysis security experts can be better prepared for dealing with a threat than before. They can tackle future attacks efficiently. Since you'll perform a regular scan on your Endpoint Threat Analysis, it helps secure your businesses from the latest threats.
How Does It Work Endpoint threat analysis?
Organizations can perform practical endpoint threat analysis by identifying all the endpoints requiring continuous analysis. Endpoint Threat Analysis means monitoring all the endpoints, such as servers, cloud-based services, mobile devices, computers, etc. After identifying endpoints, security analysts need to analyze potential threats and vulnerabilities.
Organizations can perform practical endpoint threat analysis by identifying all the endpoints requiring continuous analysis. It means monitoring all the endpoints, such as servers, cloud-based services, mobile devices, computers, etc. After identifying endpoints, security analysts need to analyze potential threats and vulnerabilities.
Two common methods used to perform Endpoint threat analysis on endpoints are:
- Penetration testing
- Vulnerability scans
The Endpoint Threat Analysis purpose of scan and test is to identify potential weaknesses and breaches in your system. You'll know what loose Endpoint Threat Analysis you need to tighten before cybercriminals can exploit them in any way.
Conclusion - Endpoint Threat Analysis
Endpoint threat analysis is quite crucial for every business regardless of its scale. It helps you identify threats and malicious activities on your endpoints. Your organization must perform regular vulnerability scans and penetration testing across all endpoints. Either rely on your cyber security team or install a powerful EDR. The Endpoint threat analysis aims to identify the system's weaknesses and vulnerabilities and prevent an attack.
The problem is that a cybersecurity team can only monitor some endpoints 24/7. There is a need to go with an endpoint Detection and Response solution, which can offer you peace of mind that no cybercriminal will exploit any vulnerable endpoint.
Are you looking for the most effective EDR? Consider getting Xcitium EDR - it lets you detect, prevent, and respond to a cyber attack better than other endpoint threat analysis tools.
