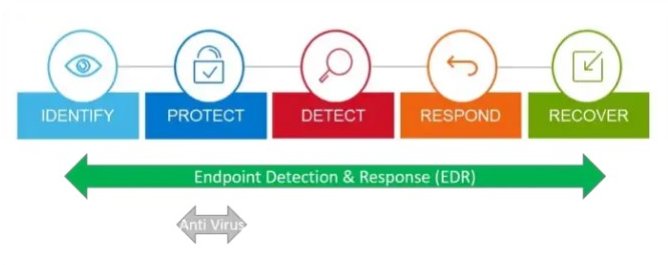
The adoption of cloud-based resources, better employee mobility, and the proliferation of capable opponents have prompted organizations to heighten their network and EDR cybersecurity. What is EDR cybersecurity? It refers to the tools and best practices that protect endpoint devices. One way to do it is by implementing an endpoint detection and response tool. Unlike traditional antivirus technology, EDR has additional monitoring and detection skills. It assumes that attackers often get past the primary layers of defenses, so it detects these incidents, addresses them, and ultimately restores the environment to how it was before the attack.
EDR Cybersecurity and Its Primary Purposes
EDR tools are generally required by EDR Cybersecurity to carry out the following tasks:
1. REAL-TIME VISIBILITY
Robust EDR solutions have real-time visibility as their core capability. They capture a wide range of data and enable real-time insight throughout the entire organization. They can produce endpoint data and combine it with machine learning to detect stealthy threats as soon as they evade your defenses. It helps you eliminate sophisticated attacks before they cause irreversible damage to your organization.

2. Telemetry Collection
It refers to the process of gathering relevant information from the endpoint devices in your network. It is usually a record of files, processes, memory, network connections, user activity, and system configuration. You can perform it locally on the endpoint and regularly send it to a centralized location.
3. Intelligent Filtering
EDR security can filter out false positives. It can minimize alert fatigue or when security agents have become desensitized to notifications, making them unable to respond to essential warnings.
4. Exploratory Data Analysis
After collecting the data from all the endpoint devices in your network, the analyst will examine them. They will relate it to the various queries in their database to check if elements of malicious software are present in the network.
5. Analytics and Enrichment
Apart from the interaction with the analyst, EDR tools will also execute an independent examination to trigger alerts based on security use cases. It may include applying machine learning techniques to aid anomaly detection or predictive modeling.
This process can be further improved when the EDR software is combined with third-party threat intelligence feeds and malware sandboxes.
6. Response Capabilities
The EDR system will offer different responses to support investigation or containment when an alert goes off. Responses may include the following:
- Endpoint restrictions
- Triggering additional data collection for further analysis or law enforcement
- Other pre-determined response plans
EDR software has automation capabilities that deliver a swift solution whenever an incident arises. It isolates an infected endpoint from the rest of the network to prevent the virus from spreading.
How to Evaluate EDR Cybersecurity Vendors?
Take the time you need when choosing your solution. Make sure that it fits exactly what your organization requires. Remember these tips while shopping for your EDR Cybersecurity.
1. What Features Do They Provide?
Most security agents deploy various techniques to scan files, watch behaviors, determine available attack surfaces, and identify if the file encountered is good or bad.
The process of reporting varies based on the EDR tool. That said, you need to ask vendors the techniques they use to determine the level of threat and actions they take in reporting or alerting your organization. From this, you can see if they meet your expectations.
2. How Do They Address Incidents?
Although EDR cybersecurity tools do an excellent job in reporting and alerting incidents, the level of response done by your security team is more important.
If the security agent gives little information for decision-making, this won't be that useful to the technical staff resolving the issue.
Technicians need security tools that display comprehensive alerts, reports, and visibility. Solutions with more comprehensive API help you review incidents better with additional information.
Does The What is EDR Cybersecurity Integrate With Other Existing Tools?
The EDR solution should fit the strategy of your Security Operations Center (SOC). It should also integrate with threat intelligence feed to identify, block, and effectively remediate attacks.
Final Thoughts on What is EDR Cybersecurity?
What is EDR cybersecurity? It keeps you protected from potential attacks and damage.
The endpoint detection and response tool is an integrated hub that collects, correlates, and analyzes endpoint data. It also coordinates with your security team to coordinate alerts and remediate threats.
Why is it essential to implement EDR in your network?
First, it protects your valuable data from being breached. Second, it helps you comply with security regulations. Third, having extra layers of protection can increase your security footprint. Lastly, it can give peace of mind to your customers, subsequently increasing your revenue.
Secure your network now with Xcitium!
Statista's Cybersecurity Outlook states that the cost of cybercrime will increase from $8.44 trillion in 2022 to $23.84 trillion by 2027.
We expect an increase of USD 11.22 Billion by 2028 in the EDR Cybersecurity solution market; Source.
Endpoint detection and response is a comprehensive endpoint security software that combines forensics, data analysis, data collection, and threat-hunting tools into one dashboard. The ultimate goal of this program is to find and block any potential threat before it causes any damage.
This system is created to detect and respond to advanced malware, zero-day attacks, and Advanced persistent threats promptly. Besides, it helps your security team investigate attacks and incidents in detail to prevent future attacks.
Let's dive into the key components and benefits of EDR Solutions.
Key Components of Cyber Security Software EDR
These days, your organization can find a wide variety of EDR vendors. Most offer the following components in their system.
Endpoint Data Collection
An EDR agent is installed on a machine and collects all the behavioral-based data from the endpoints. Whether you have endpoints on the cloud or on-premises, Xcitium offers you visibility to them from a centralized location. It collects real-time data, so your analyst can review and analyze it later.
- Data Analysis and Forensics
- Threat Hunting Capabilities
- Automated Threat Response
Data Analysis and Forensics
Once a database of endpoint behavioral activities is established, this cyber security software highlights potential irregularities. It is designed with machine learning and AI algorithm. As a result, it can differentiate between normal user behavior and malicious behavior.
The forensic functionality of an EDR solution is above average. It can detect known threats by matching its code with an existing malware database.
As far as unknown malware detection is concerned, it's where algorithms identify an unusual behavior through a threat intelligence feed. Everything happens in real time. Thereby, threat actors can't initiate an attack on your organization as this advanced system constantly monitors their activities.
Threat Hunting Capabilities
An EDR Cybersecurity Software Empowers threat hunters with all the tools and technologies they need to hunt cyber criminals proactively. They get complete visibility into all endpoints activities.
As soon as an activity seems suspicious, they can perform deep analysis and spot potential threats before they cause any damage.
Automated Threat Response
It is the essential component of an EDR solution, allowing your security analyst to analyze threats in detail without worrying about the timeframe. The tool automatically contains the threat and temporarily isolates compromised endpoints so that IT Administrator can quickly look into malicious files and attackers. Also, to stop penetration of malware into the overall network.
Since an Endpoint detection solution keeps a complete database of activities, the incident response team can quickly respond to a threat. They don't need need to perform the manual task of data collection. Every information they need about the attack is only a search filter away from them.
The Benefits of EDR Cybersecurity Software
If you want to know the real benefit of the EDR tool, then it's always suggested to compare it with traditional security options. This advanced tool is good at hunting threats in this dynamic era where threat actors are brilliant and know how to get past standard security measures. Here are some benefits you can get from an endpoint detection and response system:
• Enhanced Visibility
Installing the Xcitium EDR agent in your network offers your team a chance to make the most of high-level visibility into all endpoints. They can check what's happening on every endpoint from a single dashboard. It allows them to respond faster to threats.
• Advanced Threat Detections
Today, your organization is dealing with advanced threats such as zero-day attacks, phishing, polymorphic malware, and APTs.
According to IBM, 28% of organizations encountered ransomware attacks in 2022, while 17% suffered a breach because their business partner account was compromised.
EDR Cybersecurity solutions are designed with AI and machine learning algorithms. Thereby, they can look into suspicious behavior of unknown types of malware. These technologies can spot malicious behavior on endpoints and let your in-house team respond to a potential threat on time.
• Security for Remote Users
After covid-19, many employees started working remotely. Your organization might have a robust security system on the premises. But what about cloud-based users and remote employees?
You should know that remote endpoints are key entry points for cybercriminals. They access employee credentials, get control of a remote endpoint, and then use it to initiate an extensive network-wide attack.
The most significant advantage of Xcitium EDR is that it creates a security shield around all the endpoints regardless they are connected to your network on-premises or remotely. You can also get a hybrid solution.
Cybercriminals won't be able to take advantage of any existing vulnerabilities on your remote endpoints because EDR cybersecurity software will identify system vulnerabilities and patch them on time.
Wrap up
EDR cybersecurity is the best solution for an organization seeking endpoint protection. It lets your IT team detect and respond to malware quickly. Besides, Xcitium EDR makes it easy for enterprises to spot APTs, file-less malware attacks, and other advanced threats without spending much less time and effort.

