What is Defense in Depth (DiD)?
Defense in Depth, often abbreviated as DiD, is a cybersecurity approach that relies on a layered system of defenses to protect data, systems, and networks. Rather than depending on a single tool or security measure, this strategy involves deploying multiple layers of security technologies, protocols, and processes throughout an organization’s environment. The goal is to provide redundancy and increase the likelihood that if one layer is bypassed or fails, other layers can still prevent or mitigate an attack.
The concept of Defense in Depth originates from military strategy, where it refers to the use of multiple defensive positions spread out to slow down and weaken an attacking force. In the digital world, this idea translates to layering defenses at every level of the IT ecosystem, including network infrastructure, endpoints, applications, data storage, user access, and monitoring systems. Each layer has its own role and contributes to the overall security posture of the organization.
For example, at the perimeter, firewalls and intrusion prevention systems (IPS) might be used to block malicious traffic. Inside the network, segmentation and internal firewalls can limit the spread of threats if an intruder gets in. On individual devices, antivirus software, application controls, and endpoint detection tools provide another level of protection. Additionally, encryption and access controls safeguard sensitive data, while security awareness training ensures that employees recognize and avoid social engineering attacks like phishing.
What makes Defense in Depth effective is not just the use of different technologies, but the idea that they are strategically placed to protect against a variety of attack methods. A well-designed DiD strategy accounts for both known and unknown threats and includes proactive elements like vulnerability management, as well as reactive components such as incident response plans. This comprehensive view acknowledges that breaches may still occur, but ensures that the organization can respond quickly and limit the impact.
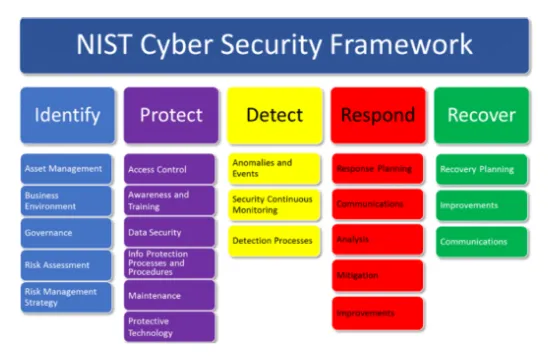
Defense in Depth also plays a crucial role in meeting compliance standards and regulatory requirements. Frameworks like NIST, ISO 27001, and PCI DSS often encourage or require layered security measures to ensure proper protection of sensitive information.
Overall, adopting a Defense in Depth strategy demonstrates a mature and forward-thinking approach to cybersecurity. It helps organizations build resilience, protect their reputation, and maintain business continuity even in the face of sophisticated cyberattacks.
Why is Defense in Depth (DiD) Important in Cybersecurity?
Defense in Depth (DiD) is important in cybersecurity because it provides a strategic and practical way to manage risk in an environment where threats are constantly evolving. Relying on a single line of defense is no longer sufficient. Attackers are more sophisticated than ever, and vulnerabilities can exist in places that are often overlooked. DiD acknowledges this reality and builds a multi-layered shield to protect digital assets, making it harder for threats to succeed and easier to respond when they do.
One of the key reasons DiD is so valuable is because it helps reduce the likelihood of a complete system compromise. If an attacker manages to bypass a firewall, for instance, additional layers like endpoint protection, internal segmentation, and behavior monitoring can stop them from moving further into the network. This redundancy is not a sign of inefficiency—it's an intentional design to slow down attacks and give defenders more time to react. The goal isn’t just to block intrusions but to detect and respond before serious damage is done.
DiD is also important because it supports business continuity. Cyberattacks can disrupt operations, damage reputations, and lead to significant financial losses. With multiple layers in place, organizations are better positioned to contain incidents and maintain critical functions during a breach. This kind of resilience is crucial, especially for industries that manage sensitive data or operate under strict regulatory requirements.
In addition, DiD improves visibility across the IT environment. Each layer—whether it’s a firewall, an endpoint detection system, or a security information and event management (SIEM) platform—provides valuable data and context. When these tools work together, they create a clearer picture of what’s happening across the organization. This helps IT and security teams make better decisions, investigate threats more effectively, and strengthen weak spots.
Another important aspect of DiD is its adaptability. As new threats emerge, new layers can be added or updated without having to overhaul the entire security architecture. This flexibility allows organizations to evolve their defense strategy over time, which is essential in a landscape where yesterday’s best practices can quickly become outdated.
Ultimately, Defense in Depth isn’t just a technical model—it’s a mindset. It reflects a mature approach to cybersecurity that assumes compromise is possible and prepares for it. Organizations that embrace this approach are more likely to withstand attacks and recover quickly, protecting not only their systems but also their people, partners, and reputation.
Real-World Examples of Defense in Depth (DiD) in Action
Real-world examples of Defense in Depth (DiD) in action help illustrate how layered security works to protect organizations from various types of cyber threats. These examples show that no single security tool is enough on its own, and that multiple controls working together are far more effective in stopping or minimizing attacks. From large enterprises to government agencies and even small businesses, DiD strategies have played a key role in preventing data breaches and limiting damage when attacks occur.
One example can be seen in financial institutions, which are frequent targets of cybercriminals. A bank might use firewalls to prevent unauthorized external access, intrusion detection systems (IDS) to monitor for unusual behavior, and encryption to protect customer data in transit and at rest. In addition, employees are required to use multi-factor authentication (MFA) and undergo regular security awareness training. If an attacker successfully steals login credentials through a phishing email, MFA can block access. If that fails, endpoint detection and response (EDR) software might detect and contain the threat before it spreads to other systems.
Another example is in the healthcare industry, where protecting patient data is both a security and compliance priority. Hospitals often rely on network segmentation to separate administrative systems from medical devices, minimizing the risk of lateral movement if a system is compromised. Medical records are encrypted and access is strictly controlled using role-based permissions. Security monitoring tools provide real-time alerts, while backup systems ensure that data can be quickly restored in the event of ransomware or other attacks. These multiple layers work together to protect sensitive information and keep hospital operations running smoothly.
Even cloud environments benefit from DiD strategies. A company using cloud infrastructure might deploy web application firewalls (WAF) to protect applications from attacks like SQL injection, while also using identity and access management (IAM) tools to restrict who can access what resources. In addition, continuous security posture management can identify misconfigurations before they are exploited. Combined with activity logging and automated threat detection, this layered approach helps secure dynamic and distributed environments.
These examples show that Defense in Depth is not just a theory—it’s a proven strategy used by organizations across industries to stay ahead of cyber threats. Each layer plays a part in strengthening the organization’s security posture, making it harder for attackers to succeed and easier to contain threats when they arise.
Best Practices for Implementing a Defense in Depth (DiD) Strategy
Implementing a Defense in Depth (DiD) strategy requires careful planning and a clear understanding of how to layer security controls effectively across your organization’s infrastructure. While the goal is to create multiple barriers that protect against different types of threats, it’s important that these layers complement each other and form a cohesive defense system—not a patchwork of disconnected tools. Following best practices can help ensure that your DiD strategy is both effective and sustainable.
One of the first best practices is to start with a comprehensive risk assessment. Understand where your critical assets are, how they’re accessed, and what threats they face. This process helps you prioritize your defenses based on actual risk, rather than making assumptions or overinvesting in one area while leaving others exposed. Once you have a clear picture, you can design your layers to address specific vulnerabilities and threat vectors.
Next, focus on securing each layer of your infrastructure individually while ensuring they work together as part of a broader defense system. At the perimeter, this might include firewalls and intrusion prevention systems. On the internal network, implement segmentation to prevent threats from spreading. For endpoints, deploy antivirus, endpoint detection and response (EDR),and device control. Don’t forget to secure applications with input validation and patch management, and to protect data with encryption, backups, and access controls.
User access control is another essential part of a DiD strategy. Use the principle of least privilege (PoLP) to ensure users and systems only have access to what they need to do their jobs. Multi-factor authentication (MFA) should be used for all critical systems and accounts. Regularly reviewing and revoking unnecessary privileges helps reduce the risk of insider threats or account compromise.
Monitoring and response capabilities are also critical. Security information and event management (SIEM) platforms can aggregate and analyze logs from across your environment, helping detect suspicious activity. Coupled with automated response tools and a well-documented incident response plan, your team will be better prepared to respond quickly and contain threats before they cause serious harm.
Lastly, don’t overlook the human element. Regular security awareness training for employees can greatly reduce risks from phishing, social engineering, and careless behavior. Everyone in the organization should understand their role in keeping systems secure.
By following these best practices, you can build a Defense in Depth strategy that not only protects your organization from today’s threats but is flexible enough to adapt as new challenges arise.
Defense in Depth (DiD) vs Single Layer Security Approaches
Comparing Defense in Depth (DiD) to single layer security approaches highlights why relying on just one line of defense is often not enough in today’s threat landscape. While a single security measure might stop some basic attacks, modern cyber threats are more sophisticated, persistent, and capable of bypassing traditional protections. DiD provides a multi-layered approach that increases resilience and minimizes the risk of a full-scale compromise.
Single layer security refers to using just one main security control—such as a firewall, antivirus software, or endpoint protection—to defend your systems. While these tools can be effective at stopping certain threats, they have limitations. A firewall, for example, might block unauthorized access at the network perimeter, but it can’t stop threats already inside the network or detect suspicious behavior on an endpoint. Similarly, antivirus software may catch known malware but often misses new or sophisticated attacks that don’t match existing signatures.
The problem with a single layer is that once it’s breached or bypassed, there’s little to nothing standing in the way of an attacker. It’s like locking your front door but leaving your windows open. Cybercriminals are constantly finding new ways to exploit vulnerabilities, and no tool is perfect. A single point of failure leaves your entire system exposed if that one defense fails.
In contrast, Defense in Depth uses a combination of overlapping security measures across different parts of the IT environment. This might include perimeter defenses like firewalls, network segmentation to limit lateral movement, endpoint detection and response (EDR) tools to catch suspicious behavior, access controls to restrict who can reach sensitive data, and security monitoring to provide real-time visibility. Each layer supports the others, making it more difficult for attackers to move undetected or achieve their goals.
Another advantage of DiD is that it provides more time to detect and respond to an incident. Even if an attacker gets past one layer, the additional layers increase the chance that the activity will be flagged before serious damage is done. This is especially important in targeted attacks or advanced persistent threats, where stealth and patience are common tactics.
Ultimately, while single layer security might seem easier or more cost-effective in the short term, it offers limited protection and high risk. Defense in Depth is a more strategic and realistic approach to cybersecurity. It reflects an understanding that breaches are possible and that the best way to stay secure is by building multiple lines of defense that work together to protect systems, data, and people.
How Defense in Depth (DiD) Supports Compliance and Risk Management
Defense in Depth (DiD) plays a critical role in helping organizations meet compliance requirements and manage cybersecurity risk more effectively. As regulations become stricter and threats more sophisticated, businesses are expected to prove that they have robust security measures in place. DiD provides the layered security architecture needed to satisfy both regulators and internal risk management teams by addressing threats at multiple levels and reducing the likelihood of a single point of failure.
Most regulatory frameworks—such as HIPAA, PCI DSS, GDPR, NIST, and ISO 27001—don’t just require a firewall or antivirus software. Instead, they mandate a range of controls that span technical, administrative, and physical safeguards. A DiD strategy aligns naturally with these requirements because it incorporates various layers of protection that touch on all areas of the IT environment. For example, encryption protects data at rest and in transit, access controls ensure only authorized users can reach sensitive information, and monitoring tools help detect and respond to suspicious activity in real time.
By implementing a layered approach, organizations can demonstrate due diligence in protecting sensitive data, which is a central expectation in compliance audits. If a data breach occurs, having a DiD strategy in place can also help limit regulatory penalties. Regulators often consider whether a company took reasonable steps to protect information. A well-documented DiD strategy shows that security was a priority and that efforts were made to mitigate risk.
From a risk management perspective, DiD is equally important. Cyber risk isn’t limited to financial losses—it also includes operational disruption, reputational damage, legal consequences, and loss of customer trust. A single-layer defense might reduce one area of risk, but it leaves gaps in others. DiD provides coverage across multiple threat vectors, making it easier to identify where vulnerabilities exist and address them proactively.
Risk management also involves understanding the impact of various threats and prioritizing controls based on potential consequences. DiD supports this by giving security teams the flexibility to apply different levels of protection to different assets. For example, high-value systems can be surrounded by multiple access restrictions, data encryption, and continuous monitoring, while lower-risk systems can receive basic protections. This tiered approach allows organizations to allocate resources wisely and improve their overall security posture.
In short, Defense in Depth helps organizations not only comply with complex regulations but also build a more resilient and risk-aware culture. It enables proactive defense, supports audit readiness, and provides a strong foundation for long-term cybersecurity success.
Future-Proofing Your Organization with Layered Security
Future-proofing your organization with layered security is about preparing for the threats you can’t see coming. The cybersecurity landscape is constantly evolving—new attack techniques, vulnerabilities, and regulatory demands emerge regularly. Relying on a single tool or reactive strategy leaves your organization exposed to both known and unknown risks. A Defense in Depth (DiD) approach, built on layered security, ensures that you’re not just protecting your current environment but positioning your organization to adapt and stay resilient in the face of future challenges.
One of the biggest advantages of a layered security model is its flexibility. As new threats emerge, individual layers can be updated, replaced, or expanded without overhauling your entire system. This modular approach makes it easier to adopt newer technologies like Zero Trust architectures, threat intelligence platforms, or AI-powered detection tools. It also means that when older tools become less effective, they can be phased out without compromising the integrity of your overall defense.
Layered security also supports scalability. As your organization grows—whether through hiring, new locations, cloud adoption, or digital transformation initiatives—your security approach can scale with you. Rather than trying to stretch one layer thin across an expanding attack surface, you can reinforce each layer where it's needed most. This ensures consistent protection across diverse environments, including hybrid workforces, remote users, mobile devices, and cloud-based infrastructure.
Another key benefit is the ability to improve incident detection and response. The more layers you have, the more visibility you gain into user behavior, network activity, and potential threats. Security teams can correlate signals across tools and identify anomalies faster. This early detection can be the difference between stopping an attack in its early stages or dealing with the aftermath of a major breach. Layered defenses also help contain threats, reducing the blast radius if an attacker gains initial access.
Moreover, as cyber insurance providers and compliance frameworks continue to raise their standards, layered security makes it easier to meet evolving requirements. Auditors and underwriters increasingly look for evidence of comprehensive security controls, risk management programs, and proactive strategies. A DiD framework demonstrates a mature, well-documented approach to managing cyber risk over time.
Ultimately, future-proofing your organization with layered security is an investment in long-term resilience. It sends a message to stakeholders—customers, partners, regulators, and investors—that your business takes security seriously and is committed to staying one step ahead of the threat landscape.