A comprehensive endpoint security solution, endpoint detection and responses (EDR) mixes real-time, continuous monitoring and collecting of endpoint data with rules-based, automated reaction and analysis capabilities.
Anton Chuvakin from Gartner coined the phrase to characterize the new wave of security tools that use advanced levels of automation to help security teams swiftly identify and react to threats by detecting and investigating suspicious behaviours on hosts and endpoints. Thus, EDR is used by businesses to secure their databases, but sometimes all they think about is what data is collected by EDR.
Here in this write-up, we will provide you with a complete guide on the features and components of EDR, how it works and what data is collected by EDR. Keep reading!
Functioning of EDR and What Data is Collected by EDR?
After EDR software has been implemented, it will examine the actions of each user on your system using complex algorithms, storing this information and making connections between them. Technology may "detect" behavior that is outside the norm for a certain user on your system in the same manner that you may notice when something seems strange about someone close to you.
Instantaneously, the information is cleaned, enhanced, and analyzed for suspicious activity. A warning is sent when any of these symptoms are detected, and an inquiry into whether or not the impact was real is launched. The algorithms reconstruct the attack chain and trace it back to its initial entry point if the illicit activity is discovered.
To make it simpler for analysts to examine, the system then groups all data points under specific headings dubbed MalOpsTM (Malicious Operations). Customers are informed of hits and provided advice for follow-up probes and in-depth forensic analysis if they turn out to be legitimate.
When an alert is determined to be false, it is deactivated, investigation notes are recorded, and the consumers are not contacted. If we talk about what data is collected by EDR, it usually goes for malicious ones.
What Kind Of Dangers Does Edr Look For?
Fileless ransomware, malicious scripts, and stolen user credentials are all things that may be averted with the help of EDR. Its purpose is to document an adversary's methods, strategies, and processes. And it gets much deeper than that. It figures out how hackers enter your system and how they navigate once inside, from one computer to another, and ultimately to their intended target. All of these things can't happen to you:
- Malware (crimeware, ransomware, etc.)
- Without using any files, attackers
- Misuse of Authorized Software
- Users that exhibit suspicious conduct
What Are the Components of EDR?
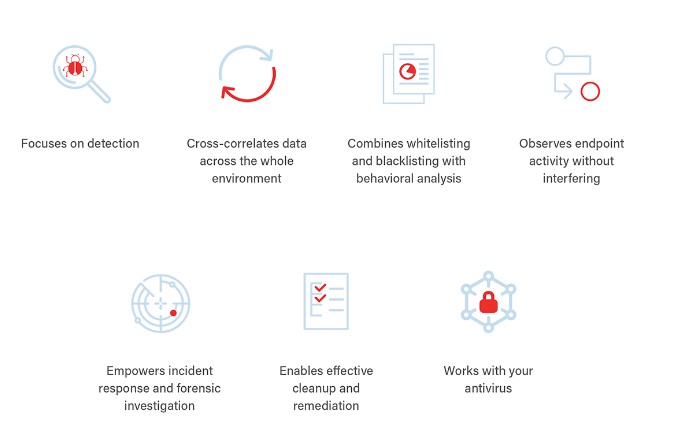
The algorithms used in EDR are what set it apart. Not only can they identify and counteract attacks, but they can also centralize the management of warnings and attack data. Immediately detecting potential threats while interfering with endpoints is made possible by using cognitive analysis to examine user activities in real-time.
Together with your antivirus as well as other security solutions, it creates a secure and safe network and helps in forensic investigations by assembling attack data into narratives that can be studied.
What Data Is Collected By EDR?
No reboot is necessary for Endpoint Detection & Response to function thanks to sensors deployed on your endpoints. This information is gathered from all endpoints, regardless of their location, and used to provide a comprehensive picture of their behavior.
Below we have broken down the answer to your question, "what data is collected by EDR." Have a look -:
- Process Information -:It collects the basic information about the process that is run through EDR to identify malicious files.
- File Information -:It also looks into the file information and makes sure to get the information collected that is needed for passing it out and keeping the databases safe.
- Connection Information -:Most data breach happens due to network issues. So, EDR collects the connection information to ensure it is secure enough to pass the data through.
- User Information -:When passing the information through EDR, it also looks for the user information to ensure that the user is verified to transfer the data and no breach occurs.
- System Information:-Among all the aspects, collecting system information is important to ensure the smooth transfer of data via EDR.
Hope now you know what data is collected by EDR and how it is done.
Why is an Effective EDR Solution Required?
As of now, you know what data is collected by EDR, so you can trust EDR for protecting your data. Still, we have something to say as to why an effective EDR solution is needed.
Enterprises and MSPs can see and stop advanced threats as they happen with the help of an EDR system. Compared to conventional methods, an EDR's array of analytical techniques is well suited to fending against sophisticated, persistent threats.
As cybercriminals increasingly target specific access points, EDRs provide a sturdier barrier to protect networks from invasion. Common security holes can be patched, saving companies millions of dollars and preventing irreparable damage to their image.
Conclusion
This inclusive guide brings much-needed information on the question of many users about what data is collected by EDR. Hope you have also found the right answer and are convinced enough to use it.