Key Differences Between Cyber Kill Chain and MITRE ATT&CK
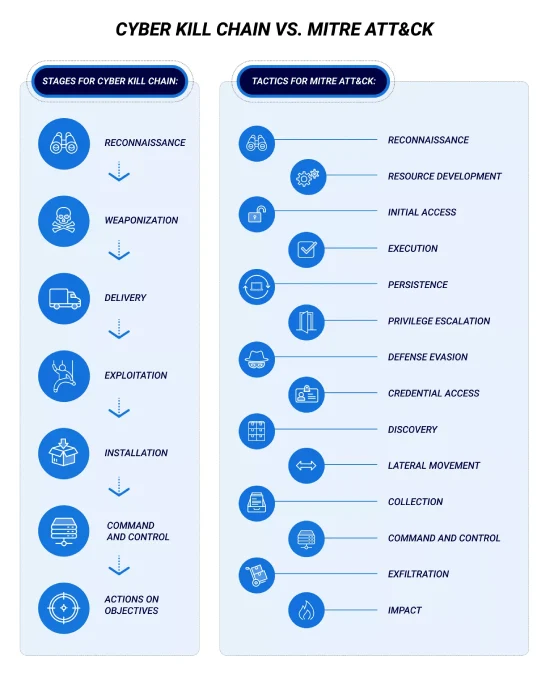
The Cyber Kill Chain and MITRE ATT&CK frameworks are both essential tools in cybersecurity, but they differ significantly in their approach, structure, and application. The Cyber Kill Chain, developed by Lockheed Martin, is a linear model that outlines the seven stages of a cyberattack, from reconnaissance to exfiltration. It is designed to help organizations detect and mitigate attacks early by understanding how adversaries operate. This model is particularly effective for perimeter defense strategies and is widely used in traditional security operations. However, its linear approach has been criticized for oversimplifying modern cyber threats, which often involve lateral movements and multiple entry points.
On the other hand, MITRE ATT&CK is a dynamic framework that provides a comprehensive matrix of tactics, techniques, and procedures (TTPs) used by adversaries. Unlike the Cyber Kill Chain, which follows a fixed sequence, MITRE ATT&CK recognizes that attackers do not always follow a predictable path. Instead, it categorizes real-world attack methods into distinct tactics, such as initial access, execution, privilege escalation, and lateral movement. This level of detail allows security teams to map threats more accurately and improve threat intelligence. MITRE ATT&CK also incorporates real-world threat actor behaviors, making it an evolving and adaptable framework that can be updated as new attack patterns emerge.
One of the key differences between the two frameworks is their level of granularity. The Cyber Kill Chain provides a broad overview of an attack's lifecycle, making it useful for high-level strategy and response planning. However, it lacks the depth required to analyze specific attack techniques. In contrast, MITRE ATT&CK breaks down each phase of an attack into specific techniques used by cybercriminals, giving security teams a deeper understanding of how attacks unfold. This makes MITRE ATT&CK particularly valuable for threat hunting, incident response, and security operations center (SOC) teams looking to fine-tune their defenses.
Another distinction is their adaptability to modern threats. Cyber Kill Chain was developed with traditional network security in mind, which makes it less effective against insider threats, cloud-based attacks, and advanced persistent threats (APTs). MITRE ATT&CK, however, continuously evolves to address emerging threats, covering various environments, including enterprise networks, mobile devices, and cloud infrastructure.
Ultimately, both frameworks serve different purposes, and many organizations use them together to enhance their cybersecurity posture. While Cyber Kill Chain offers a structured approach to understanding attacks, MITRE ATT&CK provides the technical depth needed to counter evolving threats effectively.
Which Framework is Better? Choosing the Right Model for Your Cybersecurity Strategy
Determining which framework is better—Cyber Kill Chain or MITRE ATT&CK—depends on an organization’s cybersecurity needs, existing security infrastructure, and the specific threats they face. Both frameworks provide valuable insights into adversary behavior, but they serve different purposes and are often more effective when used together rather than separately.
Cyber Kill Chain is a structured, high-level approach that simplifies the attack lifecycle into seven distinct stages: reconnaissance, weaponization, delivery, exploitation, installation, command and control, and exfiltration. This model is particularly useful for organizations that prioritize perimeter defense and need a clear framework for stopping attacks early in their lifecycle. Security teams using Cyber Kill Chain can focus on breaking the chain at any stage to prevent an attack from succeeding. However, its linear nature means it may not be well-suited for detecting sophisticated, multi-vector threats that do not follow a predictable path.
MITRE ATT&CK, in contrast, is a more granular and flexible framework that provides a detailed map of real-world attack tactics, techniques, and procedures (TTPs). Unlike Cyber Kill Chain, which follows a sequential approach, MITRE ATT&CK allows security teams to identify and respond to threats at any stage, regardless of where they occur in the attack cycle. This makes it an invaluable tool for threat hunting, incident response, and improving security operations. The framework continuously evolves with new attack techniques, helping organizations stay ahead of emerging threats.
When choosing between the two, organizations should consider their specific security goals. If the primary focus is on preventing attacks before they reach critical systems, Cyber Kill Chain can serve as a solid foundation for developing a proactive defense strategy. It is particularly effective for organizations that rely on traditional security models, such as firewalls and intrusion detection systems. However, if an organization wants a more in-depth understanding of how adversaries operate, particularly in cloud and endpoint environments, MITRE ATT&CK provides greater insights and adaptability.
For maximum effectiveness, many security teams integrate both frameworks into their cybersecurity strategy. Cyber Kill Chain helps structure a broad defense approach, while MITRE ATT&CK offers a detailed view of adversary behavior that can be used for forensic analysis, red teaming, and incident response. By leveraging both frameworks, organizations can enhance their ability to detect, prevent, and respond to threats, ultimately strengthening their overall security posture.
How to Integrate Both Frameworks for Maximum Security
Integrating both the Cyber Kill Chain and MITRE ATT&CK frameworks into a cybersecurity strategy provides organizations with a more comprehensive approach to threat detection, prevention, and response. While the Cyber Kill Chain offers a structured way to understand an attack’s progression, MITRE ATT&CK delivers granular insights into specific adversary tactics, techniques, and procedures (TTPs). When used together, these frameworks complement each other, allowing security teams to build a multi-layered defense against evolving cyber threats.
The first step in integration is mapping MITRE ATT&CK techniques to the Cyber Kill Chain stages. While the Cyber Kill Chain provides a high-level view of an attack’s lifecycle, MITRE ATT&CK fills in the details by identifying specific techniques used by attackers at each stage. For example, during the reconnaissance phase of the Cyber Kill Chain, MITRE ATT&CK details various methods adversaries use to gather information, such as phishing, OSINT (open-source intelligence),or scanning for vulnerabilities. By aligning MITRE ATT&CK techniques with the Cyber Kill Chain, security teams can better understand how attackers operate and strengthen their defenses accordingly.
Another important step is using Cyber Kill Chain as a framework for early-stage threat detection while leveraging MITRE ATT&CK for deeper analysis and response. Cyber Kill Chain helps organizations recognize and block threats at their initial stages, preventing adversaries from advancing through the attack lifecycle. However, if an attacker bypasses these initial defenses, MITRE ATT&CK provides the intelligence needed to detect lateral movement, privilege escalation, and persistence within a network. This ensures that even if an attack progresses beyond the perimeter, security teams have the visibility and tools needed to contain and mitigate the threat.
Organizations can also integrate both frameworks into their security operations center (SOC) workflows. Automated security tools, such as SIEM (Security Information and Event Management) and EDR (Endpoint Detection and Response) platforms, can be configured to detect Cyber Kill Chain stages while also identifying specific MITRE ATT&CK techniques. Threat intelligence feeds mapped to both frameworks can enhance detection capabilities and provide better context for security analysts investigating incidents.
Additionally, cybersecurity teams can use both frameworks for red teaming and threat hunting exercises. Cyber Kill Chain can serve as a roadmap for simulating real-world attacks, while MITRE ATT&CK provides detailed adversary behaviors that can be replicated in controlled environments. This approach helps organizations test and improve their defenses, ensuring they are prepared for both known and emerging threats.
By combining the structured approach of the Cyber Kill Chain with the detailed insights of MITRE ATT&CK, organizations can enhance their cybersecurity posture, improve threat visibility, and respond to attacks more effectively. This integration provides a well-rounded strategy that adapts to modern cyber threats and ensures continuous security improvements.