How Would You Get Ransomware?
Updated on October 11, 2022, by Xcitium

One of the biggest cyber threats known to mankind today has got to be ransomware. But how do you get ransomware? Considering how technology continues to evolve for the better, it’s been an insane ride for digital fraudsters, too. Cybercriminals have upped their game even more. This is because how ransomware spreads now can vary. Over are the days when common sense was all it took for you to avoid malicious malware.
That’s why for this article, we’re not just answering the question, “how do you get ransomware?” We’re shedding light on how ransomware spreads and what ransomware removal entails, too.
Let’s begin!
How Do You Get Ransomware And Who Are The Usual Victims?
Before we tend to dive right into the however does one get ransomware state of affairs, let’s cite what it’s initial. At its core, ransomware may be a malware kind that hinders a user from accessing their laptop and also the files it contains. solely then can a user be granted access to their information processing system once payment is created? That’s why it’s referred to as “ransomware.” Because, in essence, your knowledge is being commanded captive.
Still, there is no guarantee that you’re getting your data back if you shell out money. This is why of the many computer viruses there are today, ransomware can be the most emotionally stressful.
Furthermore, ransomware payments sometimes are available in the shape of untraceable cryptocurrencies, if not bitcoins. The same as our understanding of seizure, hackers set deadlines for you to form the payment. If you miss it, you’ll lose your laptop access altogether.
Over the years, ransomware variants have increased, as well. That’s why knowing exactly how ransomware spreads help you determine what to do if you face an attack. Although businesses and various government organizations are the prime victims, there have been tons of reports about individuals encountering ransomware attacks, too.
More often than not, larger organizations are what hackers target, simply because these groups of people are more likely to immediately pay a ransom. It’s also more likely for cybercriminals to charge bigger amounts of cash to agencies and businesses versus solo users.
According to a study, ransomware attacks have increased to more than 300% in the year 2019 alone! With over 60 million reported attacks, these are scary times for startups and small business enterprises to be running teams and workforces without the right digital precautions.
So, How Do You Get Ransomware?
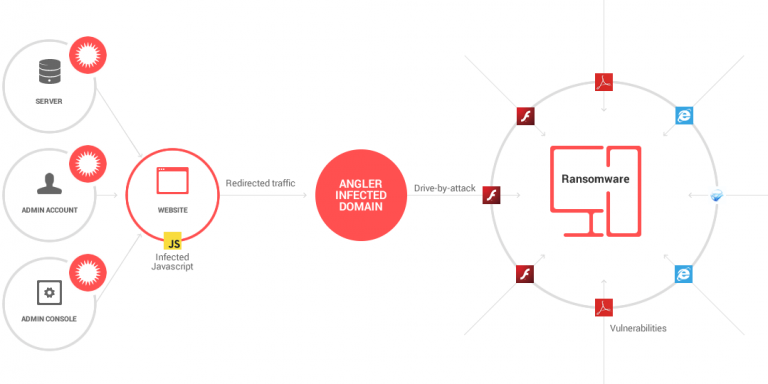
There are numerous ways your computer can get infected with ransomware, the most common one being emails that contain malicious attachments or links that lead to fishy websites.
Many times, these emails will appear to be credible, with photos looking sharp and a body of text with good writing. Once an attachment is downloaded and opened or a link is clicked, that’s where it can go downhill.
Usually, this malware type will need administrative access to start encrypting your data, but newer, more evolved versions of the malware can start encrypting files on its own.
But how ransomware spreads isn’t limited to emails alone. Removable media accessories, remote desktop connections, and social media messaging apps are also fast becoming channels for spreading ransomware.
How To Respond To A Ransomware Attack
● Speed is very important when encountering a ransomware attack. If you suspect that a malicious malware is starting to infect or take over your system, immediately disconnect it from the internet. Either unplug the cable or turn off your wi-fi connection. For safer measures, turn off other networking capabilities and Bluetooth access, too. How ransomware spreads can also be reliant on other network connections, so make sure your computer isn’t connected to anything. When you’re quick enough, ransomware removal may not even be something you’ll need to do. If you run an office or a team and suspect that other computers have been infected, do the same for every device.
● Immediately change login details! Ransomware is one quick digital beast. That being said, it can spread exponentially fast and gather important credentials and IP addresses. When that happens, fraudsters can encrypt your files, and move around your networks, access your personal email, and delete your files. So when you’re able to successfully disconnect from the internet, immediately change your login credentials. For good measure, change your account passwords, as well.
● Prepare a backup. When you have crucial data you can’t afford to lose. Always save it somewhere else. A rule of thumb for many experts is to keep important files and documents in a cloud account, on top of saving them in a flash drive or a hard drive. That way, should a hacker encrypt your data, you won’t be as worried and worked up, and you can afford to buy some time to have an expert look at your device.
● Lastly and most importantly, sign up with a reliable computer security program! When you have the support of a great anti-malware program, this shouldn’t even be a problem! Now that we’ve answered, “how do you get ransomware?” It’s time we take the necessary steps!
Sign up with Xcitium Cybersecurity today!