As cyber threats become more complex and frequent, the role of the Chief Information Security...

Understanding Next-Gen Endpoint Protection (NGEP) The words ‘Next-Gen Endpoint Protection...
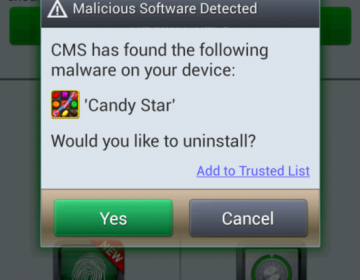
Update: check the latest version of Xcitium’s free mobile security app Have you ever heard of the...

What is DLP? Data loss prevention (DLP) is a strategy for ensuring that end-users do not send...

Shurlockr Ransomware The ShurLOckr ransomware is a malware that is like other ransomware malware,...

In the online world, cybersecurity refers to the protection of Internet-connected systems. The...

As a type of malware, ransomware attacks work like every other malware—targeting users’...

Cyber Attack through Ransomware: Here is What It Means Curious to know what is cyber-attack through...

Ransomware Attack Explained In recent years, businesses, health facilities and even government...

Computer protection or security is the process of protecting your computer against unauthorized...