Have you tried installing Windows 11 only to see a frustrating TPM-related error? You’re not...
In cybersecurity, the riskiest thing you can do is assume. Yet most vendors still operate on a...

In one of the most alarming breaches of 2025, Coinbase — the largest cryptocurrency exchange in...

In April 2025, British retail giant Marks & Spencer (M&S) fell victim to a sophisticated...

Every day, organizations face invisible threats that can disrupt operations, steal sensitive data,...

In the ever-evolving landscape of cyber threats, the recent cyberattack on Harrods, the iconic...

Adware may seem like a nuisance at first—pop-ups, redirects, and unwanted toolbars—but left...

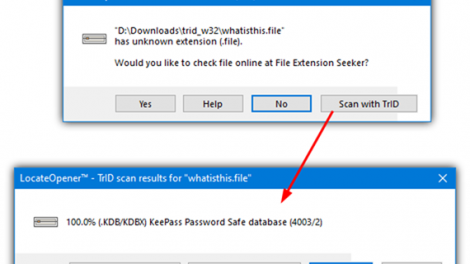
We’re here again. Another major vendor bypassed. This time? SentinelOne. A new exploit has...

Efficient, secure, and scalable IT infrastructure is critical to business success today. Managed IT...

In today’s evolving threat landscape, cybersecurity risk assessments aren’t just a best...