Everything To Learn About Vulnerability Management As A Service
Updated on January 9, 2024, by Xcitium

Cybersecurity is not any standalone service offering. As one can’t elaborate on this data monitoring, thread altering, and business-supporting network in a few words. Learning about all the services offered by cybersecurity and its prime software is like going into the deep ocean of cyber protection from all types of security interference.
The vulnerabilities of every company become the reason for numerous security breaches. It is acceptable that companies have their own security software to stop all the entries and cyber-attacks. But sooner or later they entail the need for an outsourced partner to look after all vulnerability management practices.
Why not learn more about this offering and explore vulnerability as a service (VMaaS) in today’s article? Let’s start today’s exciting voyage from here.
What is Vulnerability Management As A Service?
The inability to handle every cyber breach comes under common vulnerabilities. So, in order to detect and stop the occurrence is known as vulnerability management which indicates building an unbreakable security wall against all cyber attackers. However, due to the rapid growth of new and updated malware attacks and cybercrime as a service program, companies can’t maintain their defense against every attack.

On the urgent and needed demand of business companies and other organizations vulnerability management as a service is offered by cyber security companies. By providing agile, powerful, and expert teams, cybersecurity platforms monitor organizations’ digital environments and fix all system vulnerabilities.
Is Vulnerability Management As A Service Workable?
Outsourced platforms offering cybersecurity services are here for the needful assist of companies for the safeguarding of their cyberspaces. And this initiative of VMaaS is for strong observation, overall weakness checking, and guidance of the company’s IT workspaces.
Moreover, one of the key functions of vulnerability management as a service is to identify the malfunction and fix it before the happening of any violation by cyber attackers. Every organization working globally wants to be safe and secure with the best cybersecurity practices and that leads to availing of VMaaS from the prime player in the market. Here are some of the renowned organizations that can acquire this service.
Successful Business Enterprises
Big companies have massive sensitive data that need proper observation. VMaaS purely works for them and offers them experienced hands in cybersecurity. Famous enterprises have a major risk of losing so much exclusive data. Therefore, this service totally works for them and their network infrastructures.
SMEs & SMBs
Acquiring the best cybersecurity support is not an easy game for every company. Plus, if you are facing data breaches on a daily basis then all the leaks ask for the perfect solution in the form of VMaaS. SMEs & SMBs can’t establish their own cybersecurity teams or avail the major offerings. On that account, the solution of cost-efficient VMaaS can be hired and utilized for an instant stop to all the vulnerabilities.
Healthcare Institutions
The healthcare sector is also affected by cyber-attacks. Not only can the data of working staff and doctors be stolen, but patients’ info can also be stolen by malware attackers. So, for the sake of the unbreakable security of patients’ medical histories, healthcare institutions can hire an outsourced security team with a specialization in VMaaS.
Government Organizations
The general reveal of sensitive data also links with all the government information that has a massive chance of cyber leaks. So, security services can also be obtained by government firms; in the same way, this service offering (VMaaS) is needed for them in today’s fast-paced growing world. Hence, just for the sake of encryption of every governmental data this service is necessary.
Every Company Looking for Cybersecurity
Nowadays, secure breaches can occur in every organization, as digital exploration is part of their market growth strategies. It ultimately suggests that every company can avail of VMaaS. For a better understanding here is a list of some other sectors that can get this expert cybersecurity solution.
- Retail Organization
- Educational Institutions
- Media & Entertainment Companies
- Hospitality Industries
- Manufacturing Companies
- E-commerce Businesses
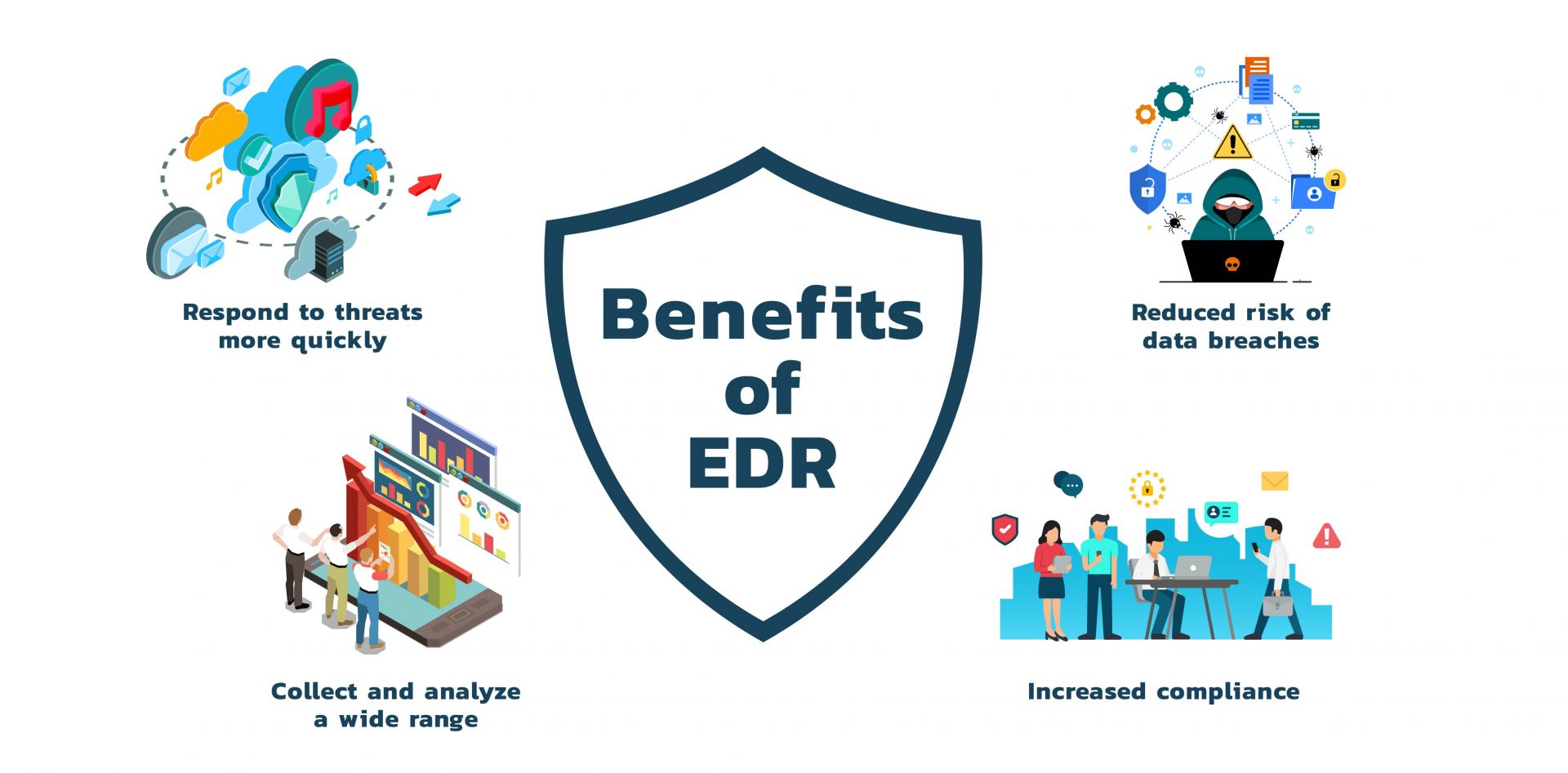
Core Advantages of Vulnerability Management As A Service
Many can link this service offering with other cybersecurity functions. Thus, this standalone service does have several advantages that must be shared with others. Every organization such as enterprises, small businesses, government sections, and healthcare institutes is open to avail all the perks by partnering with a VMaaS outsourced team.
Upgrades Security Systems
The involvement of vulnerability management experts uplifts the cyber protection of the companies asking for entailed cybersecurity help. With the guidance of those experts, every operation regarding the detection of weakness and troubleshooting actions takes place. The allocation of modern technologies and software employed by the VMaaS specialized team directly updates the security system of services availing companies.
Fast Reporting of Threat
Vulnerabilities become the open source for malware when companies don’t have a proper vulnerability management strategy. And this weakness leads to massive attacks from cybercriminals. VMaaS supports the identification of possible threats that can be harmful to sensitive data. It means this service furnishes speedy reporting under a cost-efficient package.
Rapid Diagnosis of Vulnerability
After understanding the possible weakness, the hired outsourced team troubleshoots the security flaws and reshapes it into strong cyberspace. Hence, in many cases, it takes days to completely diagnose all the vulnerabilities. However, the initial harming flaws are taken under control with rapid action.
Cloud-Based Assistance
The allocations of all VMaaS services are handled remotely and involve the cloud environment of the client companies. Plus, cloud-enabled tools also play a significant role in the effortless running of the operations performed by hired teams for the protection of client companies’ data.
Automated Scanning Assistance
In order to scan all the vulnerabilities automated tools are employed by the vendors to get faster and on-time results. This advanced technique not only keeps the systems and devices secure but also monitors their daily activities with supervising assistance.
Only Xcitium Listen To All Cybersecurity Demands
Hey, we have listened to all your cybersecurity requirements, as here at Xcitium every threat, malware attack, and security breach is altered instantly without disturbing the performance and working environment. So, are you ready to take advantage of our patented cybersecurity technologies?